"Conquer Your Risk" is a corporate blog for Cybersecurity and Risk Management executives and specialists, sharing XRATOR experts' views on Cybersecurity, Threat Intelligence, Risk Management and Cyber Insurance.
News
ENISA warns of growing cybersecurity threat caused by the geopolitics context
The European Union Agency for Cybersecurity (ENISA) published a report revealing that cyberwarfare, hacktivism, and malicious cyberattacks have transformed the...
Read moreHow the Dutch police scammed the Deadbolt ransomware gang
The Dutch police recently recovered 155 decryption keys from victims of the DeadBolt ransomware gang, revealing the hackers' creativity while...
Read moreOperation OnionPoison: pushing backdoored Tor Browser to chineses users
During regular threat hunting activities, Kaspersky identified malicious Tor Browser installers. According to their telemetry, all the victims targeted...
Read moreSophisticated Group APT36 targets India with Google Ads malvertising
APT-36, also known as Transparent Tribe and Mythic Leopard, is a Pakistan-based APT group that targets Indian government employees. Zscaler...
Read moreEmotet botnet restarts its malicious operation
On July 13th, 2022, Emotet suddenly stopped spamming in what appears to be a move to protect its victims. It...
Read moreStreaming and Piracy websites are a cybersecurity threat, NGO warns
An investigation has discovered that malicious ads on piracy sites are costing consumers $121 million by tricking people into installing...
Read moreMicrosoft OneDrive Exploited for cryptojacking operation
Cryptojacking is a form of cybercrime in which cybercriminals exploit any kind of connected devives (computers, smartphones, tablets, IOT or...
Read moreFormer CISO personally sentenced for Uber breach
The person responsible for protecting Uber's data was found guilty of inadequately safeguarding the information, which makes CISOs' personal liability...
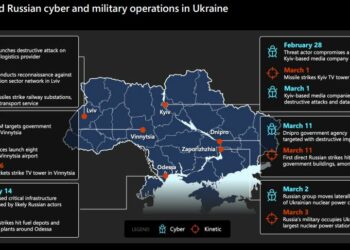
Read moreModern war: keyboards and guns
On several occasions the Russian military has coupled its cyberattacks with conventional weapons aimed at the same targets. 🚩The...
Read more