"Conquer Your Risk" is a corporate blog for Cybersecurity and Risk Management executives and specialists, sharing XRATOR experts' views on Cybersecurity, Threat Intelligence, Risk Management and Cyber Insurance.
Cyberdefense
The six pillars of the USA Strengthening American Cybersecurity Act
The Strengthening American Cybersecurity Act (SACA), signed into law in March of 2022, gives federal authorities an unprecedented look at...
Read moreArtificial Intelligence, Cyberdefense and Human Cognition
Today, in light of the growing number of cybercrimes and the sophistication of cyberattackers, companies are eager to purchase miracle...
Read moreA Cyber Security Honeypot: Everything you need to know
helpMost companies scan their networks for vulnerabilities to prevent cyberattacks. But you can also create on purpose a vulnerable system....
Read moreFormer CISO personally sentenced for Uber breach
The person responsible for protecting Uber's data was found guilty of inadequately safeguarding the information, which makes CISOs' personal liability...
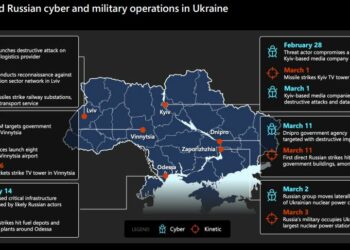
Read moreModern war: keyboards and guns
On several occasions the Russian military has coupled its cyberattacks with conventional weapons aimed at the same targets. 🚩The...
Read moreBroken links : Hundreds of Millions of Websites at Risk
Abstract External website resources can de references toward existing, expired or incorrect domain names. We...
Read moreThe H-Factor: Turning Human Into The Strongest Link Of Your Cybersecurity Strategy
Abstract Human is at the center of creation and usage of technologies; Human vulnerabilities...
Read more