The European Union Agency for Cybersecurity (ENISA) has determined and ordered the top 10 cybersecurity risks to arise by the year 2030. This report was done after they devoted 8 months to a foresight exercise. To find solutions to the upcoming difficulties by 2030, ENISA, with the assistance of the ENISA Foresight Expert Group, the CSIRTs Network and the EU CyCLONe specialists, held a Threat Identification Workshop to brainstorm.
“The mitigation of future risks cannot be postponed or avoided. This is why any insight into the future is our best insurance plan. As the saying goes: “prevention is better than cure”. It is our responsibility to take all measures possible upfront to ensure we increase our resilience over the years for an improved cybersecurity landscape in 2030 and beyond.”
Juhan Lepassaar, ENISA Executive Director
The strategic forecasting process is a key instrument to gauge how threats may change in the future. The results of this exercise are intended to prompt people to take action.
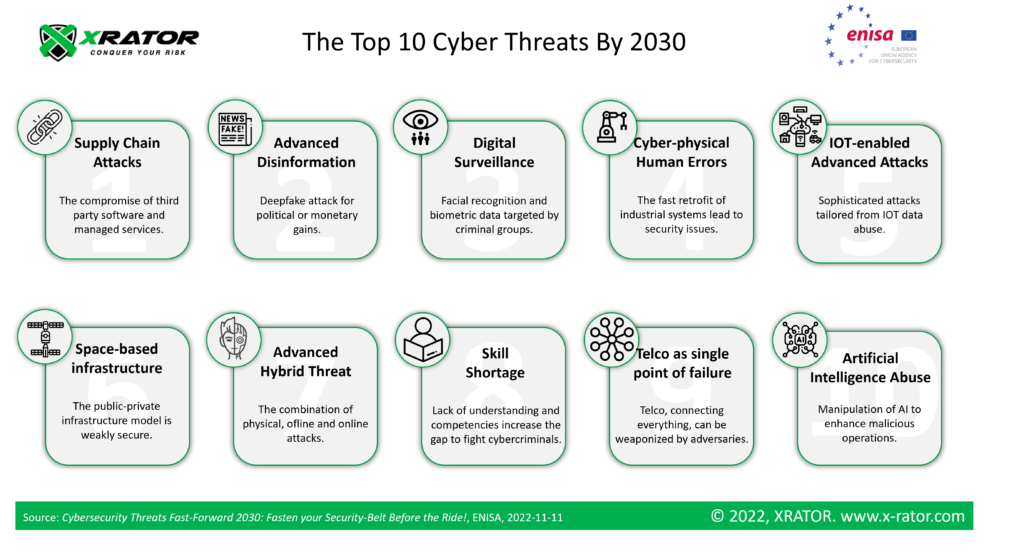 This activity demonstrates that the threats identified and ranked are highly varied and still include those that are currently most important. We can determine that the dangers which need to be addressed today will stay the same in nature, although they will have shifted over time.
This activity demonstrates that the threats identified and ranked are highly varied and still include those that are currently most important. We can determine that the dangers which need to be addressed today will stay the same in nature, although they will have shifted over time.
Additionally, we can observe that the increased reliance on computer network and the proliferation of new technologies are essential components of the changes. These elements add to the difficulty of the task and consequently make it even more difficult to comprehend the threats.
#1 – Supply chain compromise of software dependencies
Supply chain cyberattacks are one of the biggest concern of the recent years. The last couple of years demonstrates how supply chain cyber security threats can impact a full country with the danish railway cyberattack or the world with maritime traffic cyberattacks. Modern automated systems integrates and relies more and more on third party software components. The cybersecurity of a system is no more determined just by its inherent risks. Part of its cybersecurity depends of the System of Systems (SoS) in which it is part of.
Advices for software suppliers cybersecurity are a big challenges to achieve. As well as for services providers or MSP/MSSP to avoid disruption like in the Kaseya or the SolarWinds attacks.
#2 – Advanced disinformation campaigns
AI-based information and Deepfakes are one of the main concern of ENISA, fueled by the geopolitical context. The spread of bots that simulate real people can easily interfere with the public opinion, free speech and debates. From Troll factories to Fake News machinery, disinformation at the information era is both a economic segment and a political weapon.
Many people use websites such as social media, news outlets, and even search engines as their sources of knowledge. Since these websites are motivated to get more viewers, they tend to prioritize information that is more interesting which can sometimes lack credibility.
Government-supported individuals have acquired the ability to spread false information via social media sites, search engines, and messaging applications. This method contrasts with traditional disinformation strategies. These services have the capability to check and refine their material, in addition to gauging the scope and effect of their disinformation initiatives. Furthermore, progress in Machine Learning, Artificial Intelligence, artificial creations, and vocal biometrics have presented actors with potent instruments to compose deceptive content for their efforts.
#3 – Rise of digital surveillance authoritarianism
Throughout the past ten years, there has been an upsurge in worries about the proliferation of digital authoritarianism. The worldwide descent of liberty and the mounting human rights violations have exacerbated the situation. Internet neutrality has been a topic for long now. But the COVID-crisis and the use of digital tracker to fight the disease has put the debate to another level of concern.
#4 – Human error and legacy system within cyber-physical ecosystems
Cyber attacks on Industrial Control Systems by advanced threat actors already occurs, such as Stuxnet or the Triton malware. But the race of legacy factory chain an industrial machines to get ready for the Industry 4.0 thanks to digitalization does not seems to take into account cybersecurity. Fast adoption of Industrial IOT, the IT/OT convergence, the retrofit of legacy systems make the digital transformation very vulnerable to cyber attacks.
In addition, the lack of knowledge, training and skill among the workforce can leads to human errors that computerized systems can not handle properly.
#5 – Leveraging smart devices for targeted attacks
For any targeted attack, the reconnaissance phase is one of the most important for the adversary to prepare for the intrusion. This first phase of the Intrusion Kill Chain generally leverage OSINT information. External surface technical scan, gathering contact related to the victim on Social Media. Visiting target-owned websites to gather strategic information.
Smart devices and IOT devices are a new point of data collection for attackers. They can access more information before attacking the corporate network. They can access more information about the environment they have to intrude and create sharpen intrusion tools.
#6 – Lack of analysis and control of space-based infrastructure and devices
Leveraging space-related object and infrastructure in cyber attacks is not new. Notoriously, the Satellite Turla campaign hijacks satellite-based internet connection to exfiltrate data. While more recently a security researcher published its finding about the Starlink hack. The intersection of public and private infrastructure in space is an opportunity for attackers to jump for one to another. Without the burden of fighting traditional cybersecurity measures.
Cyberattacks in space or in ground station can exploit numerous opportunities. The attack can be conducting on the digital layer, on the electromagnetic spectrum, on the hardware component. Their is a huge knowledge gap between cybersecurity expert and the other. Their is a huge knowledge gap between space engineer and the other.
#7 – The rise of advanced hybrid threats
Hybrid threats are about combining several techniques of crime and/or warfare. The use of digital technologies and hyperconnectivity has led to a rise in speed, scale, and intensity of these actions. The goal of those who employ them is to damage public confidence in democratic systems, challenge the principles that societies adhere to, gain control in global issues, and reduce the decision-making capacity of countries.
Cyberattacks on cloud-storage or social platform for example can be one way among other to achieve a political, ideological, economic or criminal goal. As most of information are exchange digitally, this is where adversaries will pump to prepare other “real world” offensive operation.
#8 – Skill Shortage
According to a 2022 study Fortinet’s survey, more than 60% of respondents struggle to recruit skilled professional. From 2013 to 2021, the amount of vacant cybersecurity positions around the globe increased by 350%. It rises from 1 million to 3.5 million. 700 000 were unfulfilled in 2022.
The cybersecurity skill shortage is caused by the rapid advancements in technology and the varying risk environment. It is due to the increasing use of mobile devices, the Internet of Things, cloud computing, and data centers. We need more people, on a wider range of technologies, to counter more diverse threats types.
The skill gap between defender and attackers is growing at a fast pace for low maturity organization.
#9 – ICT Provider as a Single Point of Failure
Information and Communication s Technology provider regroups the infrastructures and the components that propels the modern computing. They connect industries, emergency services, energy. Everything. A disruption on the ICT sector, even-more if it is cross-border, can black-out large portion of population.
Recent cyber attacks like the Rackspace hack or the Winter 2023 electric shortage in Europe shows to the general public how much we rely on ICT for our daily life. Sbotage operation, network backdooring or weaponized network during conflict can leads to serious consequences on every citizen lives.
#10 – Artificial Intelligence Abuse
Advances in Machine Learning, Artificial Intelligence, deep-fakes, and voice identification have provided cybercriminals with innovative means of fabricating deceptive messages for their operations. Manipulation of AI algorithm and training data sets be used to enhance criminal operation such as the creation of disinformation, cognitive bias exploitation, or individual profiling.


