Agenda
- 1. Introduction
- 2. LockBit Business Model Breakdown
- 3. Analyzing the Affiliate Network Metrics
- 4. Geographic Insights and Market Analysis
- 5. Criminal Competitive Analysis
- 6. Prospective Evolution of RaaS Business Ecosystem & Operations
- 7. Conclusion
1. Introduction
Based on LockBitSupp recent information released by the UK National Crime agency on the 7th of May 2024, this article analyzes the effectiveness and challenges of LockBit’s affiliate program, revealing the stark discrepancy between the volume of attacks and the low success rate for affiliates. Understanding LockBit’s business model and strategies will help law enforcement and cybersecurity experts identify vulnerabilities to combat future ransomware threats.
By February 2024, Operation Cronos, an international task force, infiltrated LockBit’s infrastructure, revealing that it had facilitated over 7,000 attacks since June 2022, with only 2,110 progressing to negotiation. Despite the large volume, over half of the affiliates saw no returns, primarily due to high failure rates in negotiation. LockBitSupp, the administrator, prioritized certain “important” victims, mostly in the U.S., who were considered more likely to pay.
LockBit has rapidly emerged as a prominent ransomware group due to its aggressive tactics and sophisticated ransomware-as-a-service (RaaS) platform. It evolved from ABCD ransomware to LockBit, democratizing cybercrime by providing less technically skilled criminals with tools to carry out high-impact attacks in exchange for a cut of ransom payments. The group targeted various sectors, including healthcare and government agencies, using data exfiltration software and negotiation playbooks.
1.1. Overview of LockBit Ransomware
LockBit emerged as one of the most prominent ransomware groups over the past few years, developing a reputation for its aggressive tactics and sophisticated ransomware-as-a-service (RaaS) platform. Initially known as ABCD ransomware, it evolved into LockBit, adapting new features to quickly encrypt victims’ systems and hold their data hostage. What made LockBit stand out was its “RaaS” model, where the group’s administrators provided ready-made tools for affiliates to carry out attacks in exchange for a cut of the ransom payments. This model democratized cybercrime by allowing less technically skilled criminals to conduct high-impact attacks.
LockBit targeted a diverse range of sectors, including healthcare, manufacturing, and government agencies. The group offered affiliates tools like data exfiltration software, leak sites to publicize stolen data, and negotiation playbooks to maximize ransom payments. By mid-2022, the group had become a high-profile global threat, with attacks affecting thousands of victims and costing businesses millions in ransoms. LockBit’s relentless focus on efficiency and profitability earned it notoriety as one of the most harmful ransomware groups worldwide.
1.2. Operation Cronos Unveils Key Metrics on LockBitSupp Operation
In February 2024, Operation Cronos, an international task force led by the UK’s National Crime Agency (NCA), successfully infiltrated LockBit’s infrastructure. This effort, supported by Europol and U.S. agencies like the FBI, exposed in may 2024 detailed metrics on the group’s operations, affiliate network, and business model.

Through their cyber-forensic work, authorities gained access to LockBit’s dark web leak site and encrypted victim data, uncovering that the group facilitated over 7,000 unique attacks between June 2022 and February 2024 as well as LockBitSupp’s identity. The metrics showed that despite the volume of attacks and attempts to extort victims, only 2,110 progressed to some form of negotiation. Affiliates often struggled to profit from these negotiations, with over half seeing no return on their investment due to high failure rates.
Authorities also found that LockBitSupp, the group’s administrator, identified certain victims as “important,” marking them for specialized attention. Most of these prioritized targets were in the United States, where LockBit perceived organizations as being more likely to pay ransoms.
1.3. Article Objectives
This article aims to delve into the effectiveness and challenges of LockBitSupp’s affiliate program by analyzing the data unveiled during Operation Cronos. We’ll examine the stark discrepancies between the high number of attacks and the relatively low success rate for affiliates who invested time and resources into this criminal enterprise. By understanding how LockBit’s business model and affiliate strategies operate, we aim to highlight the risks involved in such a high-stakes scheme centralized on one figure : LockBitSupp. This analysis will also inform law enforcement and cybersecurity experts about the vulnerabilities and weaknesses in LockBit’s ecosystem, offering valuable insights into how to counteract future ransomware threats business ecosystems.
2. LockBit Business Model Breakdown
LockBit operates as a centralized Ransomware-as-a-Service (RaaS) platform, allowing a network of affiliates to conduct ransomware attacks using its tools and infrastructure, under the control of the super admin LockBitSupp. Affiliates receive comprehensive toolkits that include customizable ransomware payloads, data exfiltration software, and negotiation guides. The platform facilitates the entire attack lifecycle, directing victims to a dark web leak site for ransom negotiations while exposing non-paying victims.
Affiliates earn around 70-80% of the collected ransom, while LockBit administrators keep the rest. LockBitSupp, which identity has been revealed, oversees the network, manages ransom demands, and enforces policies. Despite the potential for affiliates to earn significant ransoms, the centralized model exposes them to systemic risk, leaving many struggling with competition, high failure rates, and reliance on LockBit’s infrastructure.
2.1. Ransomware-as-a-Service (RaaS)
LockBit operates as a Ransomware-as-a-Service (RaaS) platform, enabling a network of affiliates to conduct ransomware attacks by leveraging its ready-made tools and infrastructure. Unlike traditional ransomware groups that rely solely on internal teams, LockBit’s RaaS model makes cybercrime accessible to a wider group of criminals, democratizing the means to extort victims globally. Affiliates receive comprehensive toolkits, which include customizable ransomware payloads, data exfiltration software, and negotiation playbooks to enhance their attack effectiveness.
The infrastructure provided by LockBit facilitates the entire attack lifecycle. Affiliates deploy ransomware to encrypt a victim’s critical files and then guide victims to LockBit’s dark web leak site to negotiate payment for decryption keys. This leak site also serves as a “shaming” platform, where non-paying victims face public exposure of their stolen data. LockBit’s platform simplifies the technical challenges and risks typically associated with launching ransomware campaigns, thus broadening the criminal ecosystem to include less skilled hackers willing to operate under LockBit’s brand.
2.2. Revenue Sharing, Roles and LockBitSupp
The revenue-sharing model is central to LockBit’s RaaS operation, where affiliates and administrators divide ransom payments based on predefined percentages. Affiliates receive approximately 70% to 80% of the collected ransom, while LockBit administrators retain the remaining share, rewarding affiliates who successfully complete attacks while maintaining the infrastructure and support required to sustain operations.
At the top of this structure is LockBitSupp, the group’s super admin. He oversees the network, ensuring it runs smoothly and affiliates have the necessary tools and resources to conduct their attacks. LockBitSupp manages the leak site, decides the ransom demands, and enforces the group’s policies. Affiliates are expected to comply with guidelines to avoid targeting specific sectors or using unauthorized tactics that could attract unwanted law enforcement attention.

Despite the potential for affiliates to earn significant ransoms, the centralized model means they remain dependent on LockBit’s infrastructure and policies. LockBitSupp’s control ensures consistency but also exposes affiliates to systemic risk, where any disruption to the group’s operations could impact all network participants. The stringent revenue-sharing arrangement incentivizes only the most successful affiliates, leaving others to bear the brunt of high competition and negotiation failures.
In this high-stakes environment, LockBit’s business model has proven successful in maximizing revenue but often leaves LockBitSupp’s affiliate network struggling with high failure rates, competition, and over-reliance on a central administrator.
3. Analyzing the Affiliate Network Metrics
LockBit’s ransomware-as-a-service platform onboarded 194 affiliates, but only 148 managed to execute attacks while 46 failed to progress due to onboarding challenges or lack of technical expertise. Of those who attacked, only 119 entered negotiations, and just 80 successfully extracted payments. With 114 affiliates (59%) failing to see a return on their investment, high competition, ineffective tactics, and inadequate support led to significant drop-offs between negotiation and payment.
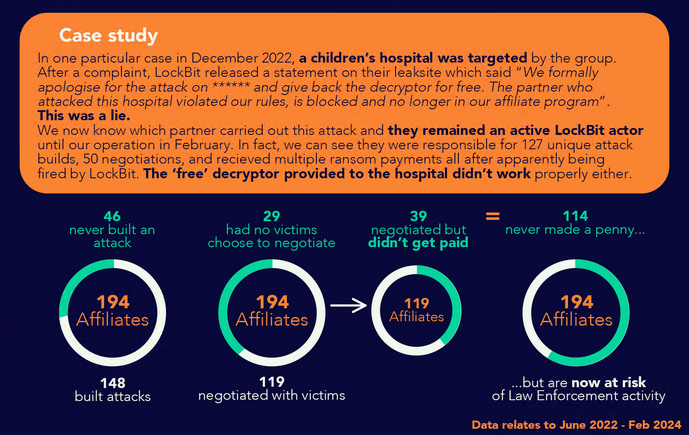
Only 41% of negotiating affiliates could convert victims into paying clients, revealing poor target understanding and weak negotiation strategies. The competition for a limited pool of targets further saturated the market and undermined affiliates’ chances of success. LockBit’s high-risk, high-failure model highlights systemic challenges, where targeting, negotiation, and diversification improvements are essential for affiliates to profit.
3.1. Affiliates Participation and Success Rate
LockBit onboarded 194 affiliates into its ransomware-as-a-service (RaaS) platform, but only 148 managed to build and execute attacks. The remaining 46 affiliates never progressed to this stage, likely due to onboarding challenges or inadequate technical expertise. Even among those who successfully launched attacks, only 119 affiliates entered negotiations with their victims. This indicates that 29 attackers failed to secure any meaningful victim engagement, likely because their tactics or targeting strategies were ineffective.
Of the 119 affiliates that entered negotiations, only 80 received payments. The remaining 39 found themselves unable to extract ransoms from victims despite their best efforts. This means that 114 of the 194 total affiliates (nearly 59%) never saw any return on their investment. These high failure rates reflect the challenges inherent in relying on LockBit’s centralized model, with many affiliates not reaching the negotiation or payment stage due to competition, poor targeting, and limited support.
3.2. Conversion Challenges
A closer look at the negotiation-to-payment conversion rate reveals further insights into why so many affiliates fail to secure returns. Only 67% of the 119 affiliates who began negotiations successfully extracted payments from their victims. This significant drop-off suggests that many affiliates either lacked a clear understanding of their targets’ psychology or employed weak negotiation tactics that were unable to coerce victims into paying ransoms.
Furthermore, this high failure rate raises questions about how affiliates prepare for negotiations and identify targets willing or able to pay. Affiliates may lack the necessary pre-attack intelligence or negotiation skills to convert potential payments into actual revenue. Some may have overestimated victims’ willingness to pay or misjudged their capacity to influence decision-makers, resulting in failed negotiations.
These challenges are compounded by competition within LockBit’s affiliate network. Affiliates frequently compete for a limited pool of profitable targets, creating internal conflicts and saturating the market with ransom demands. This saturation undermines each affiliate’s ability to effectively engage and convert victims.
LockBit’s affiliate network exemplifies the high-risk, high-failure nature of its business model. Affiliates rely heavily on centralized infrastructure and support while facing systemic challenges that inhibit their ability to earn revenue consistently. Without significant improvements in targeting, negotiation, and diversification strategies, many affiliates will continue to struggle to profit from their investment in LockBit’s platform.
4. Geographic Insights and Market Analysis
LockBit’s geographic targeting strategy illustrates a focused effort to engage lucrative markets while leveraging victim prioritization to ensure higher potential payouts from those deemed most valuable. However, the relatively low negotiation initiation rates emphasize the inherent challenges and risks of extracting ransoms even in highly targeted regions.
4.1. Top Targeted Countries
The USA and other leading markets bore the brunt of LockBit’s ransomware attacks, with the group launching 1,299 attacks against American targets alone between June 2022 and February 2024. This accounted for over 16% of the total 7,000 attacks. Following the USA, other heavily targeted countries included the UK (185), France (178), Germany (161), and China (144). The high attack volume indicates LockBit’s strategic targeting of markets believed to hold high-value, ransom-prone victims.
Despite the high attack numbers, only around 30% of these attacks (2,110) resulted in negotiations. The USA once again dominated the negotiation initiation rates, with 495 instances, followed by China (61), the UK (60), Germany (57), and Canada (53). The USA’s negotiation-to-attack conversion rate of 38% hints at a higher willingness or capacity to pay ransoms. In contrast, other regions exhibited varied conversion rates due to different negotiation strategies and risk appetites.
4.2. Victim Prioritization
LockBit’s administrators demonstrated a focused approach when marking certain victims as “important,” identifying only 72 such targets (less than 1% of all attacks). These victims were primarily based in the USA (49), with the remainder spread across Canada (8), Germany (6), Australia (5), and the UK (4).
This prioritization indicates that the group perceived high-value American targets as central to their business plan, with their significant economic, strategic, or geopolitical importance making them more likely to negotiate or pay higher ransoms.
LockBit’s selective prioritization, particularly within the USA, reveals their strategy of focusing on victims with perceived capacity or willingness to pay substantial ransoms. These “important” targets became high-stakes negotiations that could yield significant returns if successful, underpinning the group’s approach to maximize revenue through concentrated targeting.
5. Criminal Competitive Analysis
While LockBit’s RaaS model democratized ransomware operations, it oversaturated the market and imposed rigid centralized controls that left many affiliates unable to navigate competition and convert attacks into profitable negotiations. Improving data verification, specialization, and targeting strategies will be critical for affiliates to navigate the risks and rewards inherent in LockBit’s model.
5.1. Market Saturation
LockBit’s high volume of attacks, conducted by over 190 affiliates, saturated the ransomware market and made it increasingly challenging for affiliates to turn a profit. The group carried out over 7,000 attacks between June 2022 and February 2024, but only about 2,110 of these advanced to negotiation. With fewer than a third of attacks reaching negotiation and less than 20% achieving ransom payments, the competitive pressure among affiliates was palpable.
The limited pool of profitable targets, coupled with LockBit’s one-size-fits-all approach, resulted in many affiliates targeting similar victims.
This overlap led to an inefficient and crowded field where potential ransom payments were diluted, and less technically adept affiliates struggled to differentiate themselves, resulting in widespread failures.
5.2. Risk vs. Reward
The centralized model managed by LockBitSupp, the group’s super admin, exposed affiliates to significant risks while providing them with a limited reward. The LockBit infrastructure, which provided tools, guidelines, and the leak site, served as the backbone of the group’s operation. Affiliates relied on these resources to conduct attacks but faced internal competition and systemic disruption due to the group’s centralized control.
The competition for a limited pool of high-priority targets meant many affiliates lacked access to quality data and negotiation strategies, leading to suboptimal targeting and low success rates. The centralized control also made the group susceptible to external disruptions, as seen in Operation Cronos, which crippled the entire network and left affiliates unable to negotiate with victims.
This centralization imposed rigid guidelines and revenue-sharing models that failed to align with the diverse needs of affiliates, leading to a significant imbalance between risk and reward.
5.3. Comparison with Other Ransomware Groups
Compared to other ransomware groups employing the RaaS model, LockBit’s centralized structure offers both advantages and drawbacks. Its comprehensive toolkits, negotiation playbooks, and dark web leak site provided affiliates with a streamlined way to execute attacks without requiring extensive technical expertise. However, this structure created high barriers for affiliates to differentiate themselves in a crowded ecosystem. Other RaaS groups, such as Conti and REvil, struggled with similar challenges in centralization, resulting in high affiliate dissatisfaction and disputes over revenue sharing.
On the other hand, groups like Maze and Babuk adopted a more decentralized model that focused on building stronger relationships with a smaller group of trusted affiliates. This allowed them to specialize their attacks, improve negotiation tactics, and diversify their ransomware strains, reducing market saturation and enabling higher success rates. Affiliates in these groups benefitted from less competition, a more curated target selection process, and a better understanding of victim vulnerabilities, making their attacks more effective.
6. Prospective Evolution of RaaS Business Ecosystem & Operations
The future of ransomware-as-a-service (RaaS) will involve participants refining their targeting and segmentation strategies to focus on regions where negotiations are favorable and customizing demands based on economic contexts. Improved negotiation tactics, such as psychological profiling and victim behavior analysis, will enhance ransom payouts. They are also likely to diversify into other cybercrime verticals like business email compromise (BEC) or supply chain breaches. Finally, decentralized business architectures using blockchain technology could facilitate transparent revenue sharing and help affiliates adapt quickly.
To counter these trends, proactive intelligence sharing and region-specific security guidelines will be essential, alongside training incident response teams to recognize emerging tactics and simulate negotiations effectively.
6.1. Targeting and Segmentation Strategies
Affiliates need to refine their understanding of target vulnerabilities and regional negotiation preferences to improve attack success rates.
In a prospective scenario, affiliates may begin prioritizing industries and regions where negotiation cultures are more favorable, tailoring their ransom demands to align with the specific economic and cultural contexts. For instance, they might analyze local regulatory pressures, insurance practices, and business reputations to identify entities more likely to pay.
This could involve developing country-specific playbooks or collaborative intelligence-sharing networks to pool resources and identify profitable targets with higher precision.
How to monitor: Keep a close watch on patterns in the types of industries and regions increasingly targeted by ransomware groups. An uptick in attacks in emerging markets or specific sectors indicates strategic shifts. Tracking the methods used, ransom demands, and how victims are approached provides crucial insights into these patterns.
How to counter: Encourage proactive threat intelligence sharing between governments, companies, and cybersecurity vendors to identify trends early. Develop region-specific security guidelines and improve defensive measures like incident response planning. Training regional businesses to recognize and report unusual network activity promptly will also aid in early detection.
6.2. Improved Negotiation Capabilities
Adding psychological profiling and victim behavior analysis to the value chain could greatly enhance negotiation outcomes. Affiliates may prospectively employ specialized negotiation training programs to understand victim concerns around legal repercussions, reputational damage, or business continuity.
They could create victim-specific profiles to better predict responses and devise persuasive tactics. This training could be integrated into RaaS toolkits, offering data-driven decision-making guides to affiliates that maximize the perceived urgency of ransom demands.
Affiliates might even simulate negotiations to refine their strategies, leveraging machine learning models to personalize each interaction.
How to monitor: Examine emerging negotiation tactics and psychological strategies used by ransomware groups through victim feedback and forensic analysis. Analyze leaked chat logs, negotiation playbooks, and communication patterns to uncover emerging tactics.
How to counter: Train negotiators, incident response teams, and key stakeholders in recognizing these strategies. Prepare ransomware response guidelines that equip victims with tools to resist psychological pressure, and develop playbooks for quick internal decision-making to reduce delays and uncertainty during negotiations.
6.3. Diversification
Moving beyond traditional ransomware targets and exploring new markets can open fresh revenue streams and improve resilience.
A prospective scenario may involve affiliates expanding their operations into cybercrime verticals like business email compromise (BEC), Initial Access Brokering (IAB), Infostealer, and identity theft. These diversifications would enable affiliates to complement ransomware attacks with additional tactics to secure valuable data or gain insider access.
Diversifying attack vectors could include supply chain breaches, where ransomware infiltrates a target’s vendors or partners, amplifying the pressure on victims to negotiate by threatening their broader business relationships.
How to monitor: Observe changes in ransomware groups’ tactics, such as incorporating business email compromise (BEC) or supply chain breaches. Monitor dark web forums and data leak sites for shifts in target sectors and cross-vertical strategies.
How to counter: Broaden cybersecurity awareness programs to cover less traditional ransomware targets and potential breach methods. Encourage organizations to implement zero-trust architectures and vendor risk assessments while improving security for collaboration tools and email servers to thwart cross-vertical exploitation.
6.4. Decentralized Business Architecture
In future iterations of RaaS, affiliates might band together in semi-autonomous, peer-to-peer computer and business networks, where decision-making and operations are distributed, reducing exposure to systemic disruptions. Such networks could feature consensus-based protocols to determine ransom demands, distribute workloads, and share intelligence securely. These networks might even embrace blockchain technology to facilitate transparent, tamper-proof revenue sharing. Affiliates could move toward smart contracts that automatically distribute ransom payments based on predefined criteria, minimizing trust-based conflicts.
This decentralized architecture would help affiliates diversify their risk exposure and operate flexibly without reliance on a central administrator, potentially allowing them to build more specialized sub-networks targeting specific regions or industries. This evolution represents the next logical step in ransomware as a service, one that promises greater operational security, adaptability, and profitability for affiliates in an increasingly sophisticated cybercriminal ecosystem.
How to monitor: Track conversations and technological developments in decentralized protocols, particularly blockchain, on cybercriminal forums. Analyze shifting organizational structures that indicate a move towards decentralized peer-to-peer networks. Hunt for criminal purpose smart contract.
How to counter: Develop international coalitions for intelligence sharing and law enforcement collaboration. Strengthen information-sharing mechanisms with ISPs, cybersecurity firms, and government agencies to identify and disrupt these networks early. Additionally, promote security-by-design principles in emerging blockchain technologies to reduce their misuse.
7. LockBitSupp’s Leak and the future of cybercrime
The data from LockBitSupp’s affiliate program reveal a high-risk, high-failure business model where a majority of affiliates fail to profit. With over 7,000 attacks launched but fewer than 20% yielding ransom payments, competition among affiliates, poor negotiation strategies, and centralized infrastructure vulnerabilities are key challenges. LockBit’s centralized structure, under the control of LockBitSupp, creates a rigid system that exposes affiliates to systemic risks and offers little support for enhancing their success rates. Affiliates face high barriers due to internal competition and oversaturation, ultimately leading to an over-reliance on a fragile centralized ecosystem.
LockBitSupp’s affiliates and the RaaS model face growing law enforcement scrutiny, as evidenced by Operation Cronos. With more international cooperation and advanced forensics, law enforcement can increasingly infiltrate and dismantle centralized RaaS groups. In response, ransomware groups may shift toward decentralized architectures for resilience and security. Future iterations of RaaS could also see specialized affiliates employing improved negotiation strategies, targeting methodologies, and diversification tactics, thus becoming more sophisticated and potentially harder to counter. Despite these adaptations, centralized control issues and affiliate competition will continue to challenge the profitability and sustainability of this ecosystem.
While ransomware remains a lucrative market for some, high risks and low returns plague many affiliates chasing quick profits in LockBitSupp’s affiliate program. The competitive landscape, the centralized control of resources, and evolving law enforcement efforts make it challenging for affiliates to thrive. For cybersecurity professionals and law enforcement, understanding these dynamics is crucial in countering the ransomware threat and mitigating the financial and reputational damage caused by these criminal enterprises.


