The CVE-2024-3094 incident, also referred as XZ Attack, marks a significant event in the cybersecurity landscape, highlighting a sophisticated attack on the widely used XZ Utils compression tool within the Linux ecosystem. This vulnerability allowed attackers to potentially gain unauthorized access to systems across various sectors, including government, finance, and healthcare, thereby posing a substantial risk to sensitive data and critical infrastructure.
The attack stands out not only for its technical intricacy, involving multi-stage obfuscation and the embedding of encrypted payloads, but also for its exploitation of the open-source community dynamics and the mental health vulnerabilities of maintainers.
The CVE-2024-3094 incident illuminates the complex interplay between technical security and human factors in the cybersecurity domain. It underscores the necessity of addressing the vulnerabilities inherent in the open-source model—not just at the code level but in supporting the human elements that sustain these crucial projects. Strengthening the resilience of the open-source community against such exploitations requires a multifaceted approach, focusing on enhancing technical defenses, fostering community support networks, and prioritizing the mental health and well-being of those at the forefront of maintaining the open web.
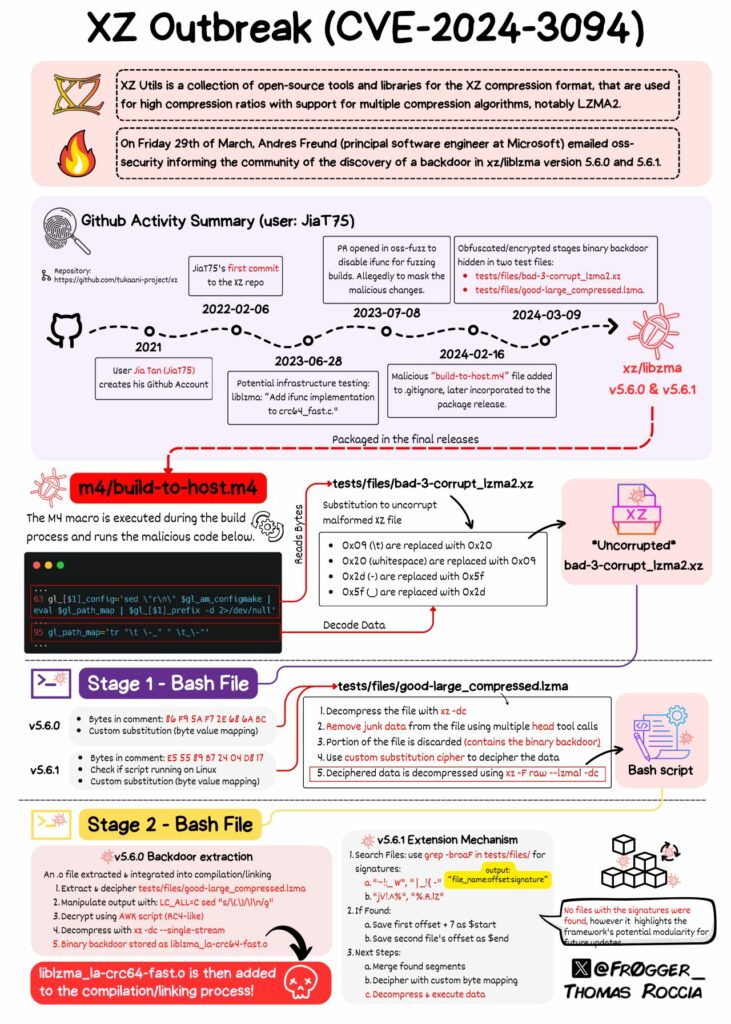
XZ Outbreak (CVE-2024-3094) summary by Thomas Roccia (@frogger) – source
Real-World Impact of CVE-2024-3094
The CVE-2024-3094 vulnerability’s impact extends across the digital infrastructure spectrum, presenting a multi-faceted risk to global systems reliant on XZ Utils for data compression tasks. The ubiquity of XZ Utils across numerous Linux distributions amplifies the vulnerability’s risk profile. Its widespread use in environments ranging from embedded systems to large-scale servers means that the potential attack surface is vast, increasing the likelihood of critical exploits.
The intrusion into XZ Utils highlights a significant supply chain risk, demonstrating how deeply embedded software components, often overlooked in security audits, can serve as vectors for wide-ranging attacks. The incident reveals the attackers’ strategic selection of targets within the software supply chain, exploiting the trust and ubiquity associated with XZ Utils to maximize impact.
The exposure of CVE-2024-3094 serves as a critical alert to the digital industry at large. It not only spotlights the sophistication and stealth of modern cyber threats but also calls for an introspective look at security strategies, particularly in the oversight of software supply chains. The incident propels a shift towards more rigorous security measures, emphasizing the need for an industry-wide elevation in security awareness and practices to preemptively mitigate similar threats in the future.
The real-world impact of CVE-2024-3094 transcends immediate data security concerns, challenging existing security paradigms and urging a concerted, industry-wide effort towards fortified digital defenses and software supply chain integrity.
Timeline and Tactics Analysis
The strategic deployment of the CVE-2024-3094 backdoor within XZ Utils exhibits a calculated blend of technical acumen and social engineering, executed over an extended timeline. This analysis breaks down the orchestrated steps taken by the attackers, led by the pseudonym JiaT75 and their collaborators, to integrate malicious code into a widely trusted open-source utility.
The orchestration of CVE-2024-3094 serves as a stark reminder of the complexities and vulnerabilities inherent in maintaining open-source projects. The detailed timeline and tactics employed by the attackers highlight the need for heightened vigilance, both in terms of technical safeguards and the social dynamics of open-source communities. This incident prompts a reevaluation of contribution and maintenance practices to safeguard against such sophisticated and long-term infiltration strategies in the future.
Preliminary Phase: Building Trust and Establishing Presence
Initial Contributions: The attackers began their campaign by making benign contributions to projects related to XZ Utils. These initial forays served dual purposes: first, to mask their true intentions under the guise of genuine contributions; and second, to build a reputation within the community as trustworthy developers.
Social Engineering: Concurrent with their contributions, the attackers engaged in strategic social engineering efforts. By interacting with key community members, they gradually ingratiated themselves within the community, gaining trust and access to more sensitive aspects of project development.
Middle Phase: Strategic Placement and Role Acquisition
Exploiting Community Dynamics: Leveraging the open-source community’s reliance on mutual trust and collaborative development, the attackers positioned themselves as integral contributors to the XZ Utils project. Their understanding of community dynamics was pivotal in bypassing the usual scrutiny applied to newer contributors.
Role Expansion: Over time, JiaT75 and associates expanded their roles within the project. By advocating for additional maintainer roles under the pretext of project enhancement and by leveraging their established trust, they secured positions that granted them unfettered access to the project’s codebase.
Final Phase: Embedding the Backdoor
Code Injection: With sufficient access and trust, the attackers began the process of embedding the backdoor. This was done subtly, incorporating malicious code within legitimate contributions to avoid detection by other contributors and maintainers.
Obfuscation Techniques: The malicious code was deeply obfuscated, making detection via code review exceedingly difficult. The attackers employed sophisticated techniques to ensure that the backdoor would remain undetected until its activation, highlighting their technical prowess and understanding of software development practices.
Activation and Exploitation: The ultimate goal was the activation of the backdoor to exploit vulnerabilities within systems utilizing XZ Utils. This step was meticulously planned to occur under conditions that would maximize impact while minimizing the chances of immediate detection.
Tactical Insights
The attackers’ success was largely due to their long-term planning and patience. They understood the value of building a solid foundation of trust within the community before executing their final objective.
The operation’s success was not solely due to technical sophistication but also relied heavily on social engineering tactics. The ability to navigate and manipulate community dynamics was equally crucial.
The exploitation of the open-source community’s inherent vulnerabilities—such as the reliance on trust and the challenges of thoroughly vetting contributions from numerous sources—was a critical factor in the attackers’ strategy.
Technical Analysis of the XZ Attacks
The XZ backdoor is a testament to the advanced technical methodologies employed by cyber attackers to infiltrate and compromise systems. This section dissects the layered complexity of the backdoor’s design and execution, illustrating how the attackers managed to bypass conventional defenses and obscure their tracks effectively.
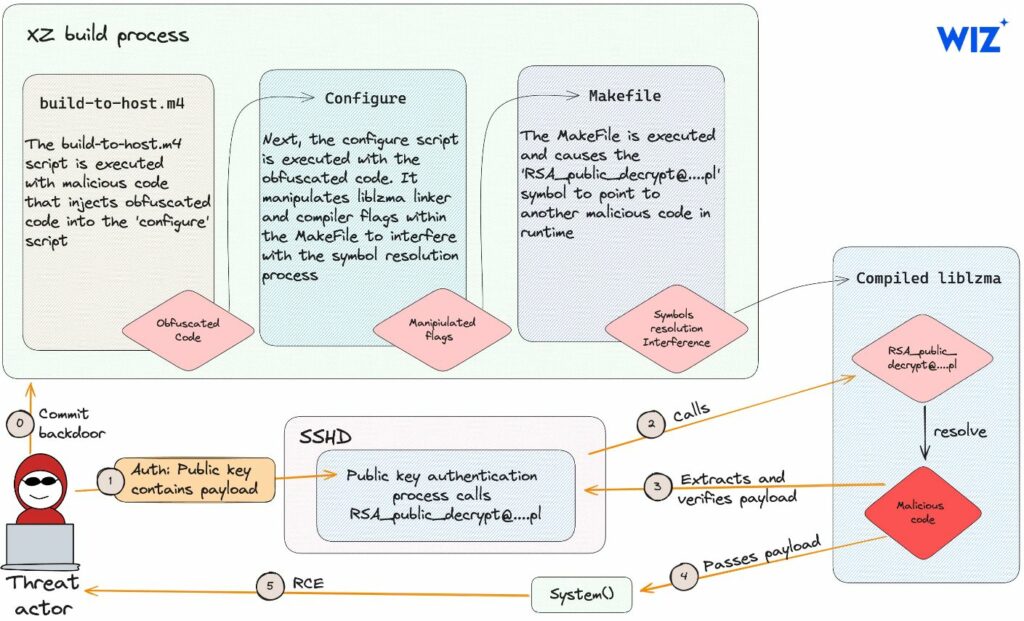
XZ build process and backdoor functionality – source
Multi-Stage Obfuscation
The attackers implemented the backdoor through a carefully structured, multi-stage process. Each stage was designed to only reveal itself under specific conditions, thereby minimizing the risk of detection at any single point. This incremental approach allowed the malicious code to embed itself more deeply into the system before activation.
Critical to their strategy was the embedding of encrypted payloads within binary test files. These payloads were designed to be decrypted and executed only at the final stage, further concealing their intent and making preliminary analysis challenging.
Leveraging Bash Scripting
The backdoor utilized bash scripting for its execution logic, allowing for the gradual unfolding of the attack. Bash scripts were chosen for their ubiquity and flexibility, enabling the attackers to craft complex execution flows that could adapt based on the environment in which they were deployed.
The bash scripts were embedded within legitimate files or appended to benign scripts, masking their presence. By piggybacking on legitimate operations, the attackers minimized the likelihood of the scripts raising alarms during routine security checks.
Bypassing Conventional Security Measures
The technical sophistication of the CVE-2024-3094 backdoor extended to its ability to evade detection by conventional security measures. Through the use of obfuscation, encryption, and the strategic use of legitimate system functions, the malicious code could remain latent, avoiding triggers that would typically alert security mechanisms.
The layered obfuscation and the encrypted nature of the payloads significantly complicated the analysis. Security researchers were required to deconstruct each stage of the obfuscation to understand the payload’s purpose and potential impact, delaying mitigation efforts.
A case of Open Source Community Mental Health Exploitation
The CVE-2024-3094 attack not only exposed technical vulnerabilities but also shed light on more insidious aspects of cybersecurity threats: the exploitation of human and community weaknesses. This segment examines how the attackers capitalized on the open-source ecosystem’s structural vulnerabilities and the mental health challenges faced by contributors.
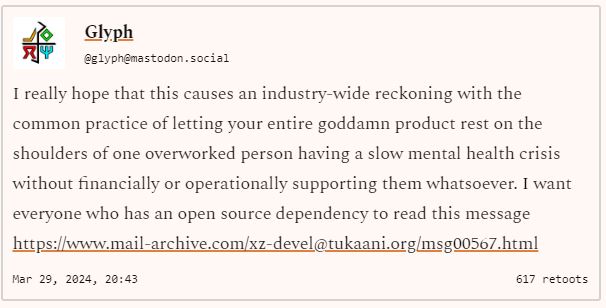
Lasse Collin message Re: [xz-devel] XZ for Java
Exploitation of Open-Source Dynamics
Reliance on Single Maintainers: Many open-source projects rely heavily on a small group of maintainers or, in some cases, a single individual. This concentration of responsibility creates a single point of failure that attackers exploited. The attackers recognized that overburdened maintainers could not scrutinize every contribution with the necessary depth, especially in projects with high volumes of contributions.
Manipulation of Trust: Trust is the bedrock of the open-source community, facilitating collaboration and innovation. However, this trust was manipulated as the attackers, masquerading as benign contributors, gradually gained the community’s confidence. This manipulation allowed them to introduce malicious code without immediate detection, exploiting the community’s inclusive and trusting nature.
Mental Health Challenges
Pressure and Burnout: The immense pressure on maintainers, often volunteering their time and expertise, can lead to burnout and mental health struggles. The attackers preyed on these conditions, knowing that stressed and overworked maintainers are more likely to overlook subtle signs of tampering or malicious intent.
Strategic Stress Induction: By creating situations that exacerbated maintainers’ stress levels, such as pushing for urgent updates or suggesting significant changes, attackers could further distract and overload those safeguarding the project’s integrity. This tactic reduced the likelihood of early detection of the backdoor, allowing it to embed more deeply within the project.
Implications for Open-Source Sustainability
Community Vulnerability: The exploitation of community dynamics and mental health vulnerabilities highlights a significant risk to the sustainability of open-source projects. It calls attention to the need for stronger support structures for maintainers and contributors, emphasizing mental health and well-being alongside technical support.
Reevaluation of Open-Source Practices: There’s a critical need to reevaluate current open-source practices, considering both the technical and human aspects of project maintenance. This includes developing more collaborative maintenance models, providing mental health resources, and implementing comprehensive security training to recognize and mitigate social engineering tactics.
Conclusion
The CVE-2024-3094 incident, or the XZ Attack, is not merely a story of technical vulnerabilities exploited with sophistication; it is a poignant narrative on the overlooked aspects of cybersecurity—human and community vulnerabilities.
This attack methodically penetrated the open-source ecosystem, leveraging not just code complexities but also the trust and pressures inherent to community-driven projects. It exposed the critical need for a holistic approach to cybersecurity, one that encompasses robust technical defenses while also addressing the well-being of those who guard the digital commons.
As the open-source community grapples with this incident, the imperative to support and protect maintainers against such exploitation becomes clear.