The act of exposing adversary tactics and infrastructure triggers a profound operational reset within these sophisticated and persistent groups, challenging the traditional cat-and-mouse game between attackers and defenders.
Real-world use cases, such as the strategic overhaul observed in APT1 following the Mandiant report in 2013 and the rapid infrastructure evolution of Predator spyware post-exposure in 2024, demonstrate the substantial impact and necessity for adversaries to pivot, underscoring the role of timely and actionable threat intelligence in disrupting cyber threat operations.
Those resilience behaviors witnessed in offensive operations also give insigth about the constraint faced by sophisticated actors while trying to reduce interruption time. If resilience is hard for the defense, it is even harder for the offense.
Rebooting Cyber Attacks: The Tactical Pause and Pivot of APT1 and Predator
Mandiant’s groundbreaking report on APT1 in 2013 marked a watershed moment in cyber threat intelligence. It provided an unprecedented level of detail on the group’s operations, tactics, and infrastructure. Following the release, APT1 significantly altered its infrastructure, pausing operations to revamp its command-and-control (C2) channels. This reaction highlighted the tangible impact of intelligence dissemination on adversarial behavior, forcing a reevaluation and adaptation of their operational framework. Looking at Mandiant’s timeline, we can see a four-month gap between the abrupt halt of APT1’s infrastructure following the public reporting and the revamping of operations.
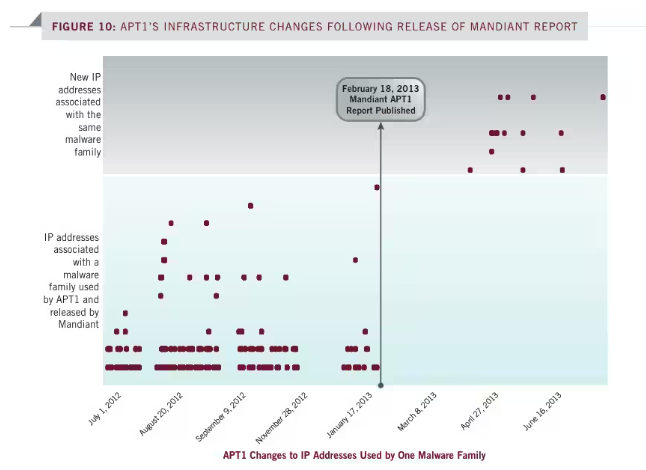
More recently, the Predator spyware saga underscores the contemporary relevance of these dynamics. After a detailed exposé by Sekoia.io in october 2023, the operators behind Predator spyware undertook a significant overhaul of their infrastructure before going active again. This behavior, reported by Sekoia at the end of february 2024 and confirmed by Recorded Future at the beginning of march 2024, not only illustrates the persistent threat posed by these actors but also showcases their resilience and capacity to evolve in response to external pressures. Such events also highlight that, obviously, if they need to evolve, it means that they are themselves facing threats: cyber defense.
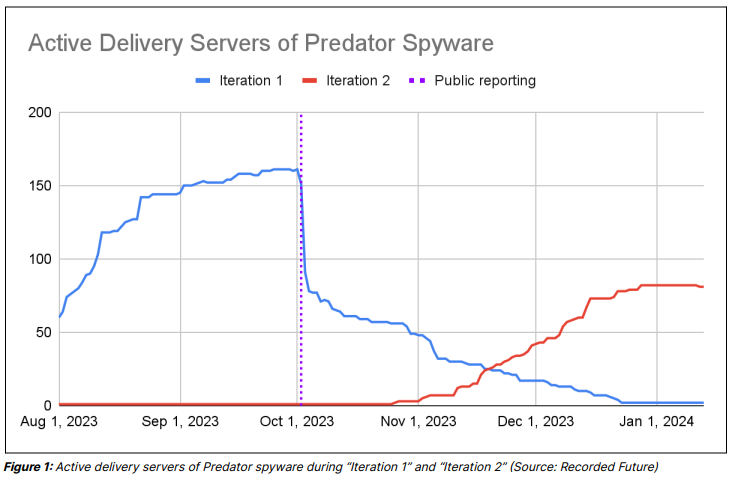
Looking closer at Recorded Future’s timeline, we can see that at the date of the public reporting, the disclosed infrastructure had been reduced by roughly half of its servers, going from about 150 to 75 active servers. Then, the total decommissioning of the remaining active servers took another two and a half months. While the fresh C2 infrastructure took roughly three weeks to start taking over, with the first activities reported in late October 2023.
While it is possible that the domains and delivery servers observed during “Iteration 1” only appeared active due to improper infrastructure takedown, the possibility that they were still being actively used for campaigns cannot be ruled out.
(Predator Spyware Operators Rebuild Multi-Tier Infrastructure to Target Mobile Devices – Recorded Future – March 1, 2024))
The investment in resilience versus the imperative for offense
The forced adaptations triggered by the APT1 and Predator spyware operations reports unveil a critical challenge that adversaries confront: maintaining operational stealth while executing expansive, enduring campaigns. The observed hiatus—spanning weeks or months—for reconstitution and revamping of infrastructure post-exposure, underscores the significant operational, technical, and strategic resources required to rebuild compromised capabilities. This period of silence is not a pause but a tactical retreat, providing adversaries the opportunity to reevaluate, redesign, and reinforce their operational frameworks to counter the enhanced detection and mitigation strategies employed by their opponents. This is also probably where lies the law of the jungle: some attackers will be able to do it and survive, some don’t and will die.
As adversaries need to balance their own effort between offensive capability and resilience, they face a cycle of adaptation that necessitates a deeper understanding of cyber defenses and an anticipatory approach to countermeasures. The need for rapid innovation in evasion techniques and the deployment of stealthier, more resilient infrastructure signifies a shift towards more advanced, adaptive cyber operations. In a word: less offensive prowess and more strategic thinking. Not only it increases the operational complexity but also requiere new competencies and human ressources needs.
This ongoing cycle of exposure and adaptation emphasizes the strategic dimension of cyber operations, where timing, resource allocation, and operational secrecy become critical factors in maintaining the upper hand. The time taken to revamp operations post-exposure is a testament to the meticulous planning and significant resources adversaries must invest to remain viable threats.
Forced adaptations extends beyond the technicalities in wich those sophisticated adversaries are often portrait, encapsulating a broader strategic confrontation in cyberspace. This confrontation is not just about the technical skills to evade detection or the capability to launch a mind-blowing cyberattacks but also about the strategic acumen to foresee, adapt, and innovate in the face of escalating cyber defense measures.
The constraint of Adversaries’ Forced Adaptation
The forced adaptations observed in the aftermath of public exposures, such as those of APT1 and Predator spyware, underscore a complex balancing act between maintaining stealth and delivering impactful cyber operations. This recalibration isn’t merely about switching servers or adopting new domain names; it’s a comprehensive operational overhaul that touches every facet of an adversary’s ecosystem.
Technical Complexity and Human Resource Constraints
The process of rebuilding compromised infrastructure reveals the multifaceted nature of cyber operations. Consider the shift from a compromised C2 infrastructure to a new, unexposed one. This is not just about erecting new servers; it involves the careful selection of hosting environments that evade blacklists (T1583 – Acquire Infrastructure), the migration and testing of C2 software to ensure compatibility and stealth (T1587 – Develop Capabilities, T1588 – Obtain Capabilities), and the re-establishment of encrypted channels for secure communication with malware implants.
For instance, after the exposure of its operations, APT1 would have needed to not only set up new servers but also ensure these servers did not communicate in patterns or through IPs that could be easily linked back to their previous activities.
The reconstitution phase likely involved deploying new encryption standards for C2 communications to avoid signature-based detection, requiring both technical acumen and a deep understanding of evolving cybersecurity defenses.
Operational Shifts in Malware Development and Deployment
Adapting to exposure demands a sophisticated approach in malware development, deployment, and update strategies. Beyond simply crafting evasion techniques to sidestep signature-based and behavioral detection by antivirus solutions, adversaries face the challenge of maintaining operational stability and stealth. This operational imperative requires them to employ practices akin to professional software development, such as rigorous version control and regression testing. Ensuring that updates to malware do not disrupt the functionality of the infected system or alert users to its presence necessitates a delicate balance between advancing offensive capabilities and preserving the integrity of the host environment.
Malware developpers must rigorously ensure that each iteration of their malware remains compatible with a wide array of target environments. This entails conducting thorough testing across different operating systems, versions, and configurations to identify potential crashes or performance issues that could signal the presence of the malware to end-users or security systems.
Additionally, developers must manage the complexity of updating malware on compromised systems without detection, which involves carefully crafting update mechanisms that avoid raising suspicions. This level of operational discipline requires a deep technical expertise, not just in crafting malicious code, but in understanding the nuances of system architectures and user behaviors to maintain stealth and functionality.
Resource Allocation and Operational Secrecy
The imperative to continuously evolve in response to threat intelligence sharing and cybersecurity advancements necessitates a significant investment in both human and technical resources. Adversaries are forced to allocate these resources judiciously, balancing the need for developing sophisticated evasion techniques with the maintenance of a secure, stealthy operational infrastructure.
This strategic resource allocation involves the cultivation of expertise in operational security to mitigate the risk of exposure. The essence of operational secrecy in this adversarial context extends beyond mere technical obfuscation techniques. It encompasses a comprehensive approach to concealing the malware development lifecycle, from initial concept through to deployment and updates, ensuring that every phase is shielded from the glaring eyes of cybersecurity researchers and automated detection systems.
Each decision to adopt a new technique or technology must represents a calculated risk, balancing the potential for increased stealth against the resource expenditure required to implement and maintain these capabilities effectively. And eventually the easiness of adaptation after a public reporting.
Toward Planned Disruption and Adaptation of Cyber Adversaries
Observations from the APT1 and Predator spyware cases underline a tangible operational challenge for cyber adversaries: the need to halt operations and undertake a time-consuming process of infrastructure overhaul following public reporting on their activities. This interruption, extending from weeks to months, significantly impacts the continuity and effectiveness of their operations.
Resilience against disruptions posed by cyber defenders is an essential facet of sustaining long-term cyber operations. This resilience requires strategic, managerial skills to assess and mitigate the nearly certain risks of detection and exposure. Theoretically, and potentially in practice among the most sophisticated adversaries, there’s a movement towards integrating these disruptions into their operational risk management strategies. By anticipating the potential for public exposure and subsequent operational disruption, adversaries can prepare staged-backup infrastructure. Such an approach would transform the recovery process post-exposure from a matter of weeks or months to merely days or even hours.
Implementing a proactive, anticipatory strategy for infrastructure resilience, while strategically advantageous, introduces significant complexities in terms of resource allocation, maintenance, and overall operational costs for adversaries. The primary counterpoints to such an approach underscore why it’s not universally adopted or straightforward to implement:
- Resources intensification. Adversaries must procure additional servers, domains, and encryption tools, often requiring diversification to evade blacklisting and other security measures. This expansion necessitates a larger financial outlay and an increase in the logistical complexity of managing multiple infrastructures simultaneously.
- Maintenance and Upkeep. Beyond initial setup, the continuous maintenance of a ready-to-deploy backup infrastructure significantly strains operational budgets. The technical manpower required to maintain operational readiness, alongside their primary infrastructure, amplifies the challenge, necessitating a dedicated team for upkeep, which in turn increases the risk of exposure and operational slip-ups.
- Complexity and Coordination. The transition from compromised to backup systems must be seamless to avoid detection, requiring sophisticated command and control mechanisms and secure communication channels. This complexity can increase the likelihood of errors, potentially compromising the backup infrastructure even before its activation.
- Opportunity cost. Resources dedicated to this endeavor could otherwise be utilized for enhancing offensive capabilities, exploring new vulnerabilities, or expanding into new target domains. The balance between resilience and offensive expansion becomes a strategic consideration, with each choice having its own set of implications for long-term operational success.
- Stealth versus Adaptation. The more extensive the infrastructure, the greater the digital footprint, potentially increasing visibility to cybersecurity researchers and defenders. Adapting to evolving cybersecurity defenses while managing an increasingly complex infrastructure requires not only technical agility but also strategic foresight, further complicating the adversaries’ operational playbook.
Despite the apparent benefits of integrating staged-backup infrastructures into operational planning, the implementation is not ubiquitous among cyber adversaries. The decision to adopt such a strategy involves a careful evaluation of its benefits against the inherent risks, costs, and complexities, which may explain the variance in its adoption and the ongoing evolution of adversary tactics in response to the dynamic cybersecurity landscape.
Conclusion
Recognizing the significant resources, time, and complexity involved in adversary adaptations to public exposures and infrastructure overhauls presents defenders with unique opportunities to disrupt and deter malicious activities. By focusing on the dissemination of threat intelligence, enhancing public-private collaborations, and investing in advanced detection and response mechanisms, defenders can increase the cost, complexity, and risk associated with offensive cyber operations. The insights gained from analyzing adversarial adaptability in the face of exposure and infrastructure overhaul highlight a critical advantage for defenders: the strategic imposition of operational costs on adversaries.
The ability of defenders to impose operational costs on adversaries is a needed strategic shift in the landscape of cybersecurity. It is about actively shaping the operational environment to the detriment of adversaries. The strategic use of threat intelligence, collaboration, and technology not only disrupts adversaries but also forces them into a defensive posture. This proactive defense strategy, rooted in a deep understanding of adversarial challenges, turns the tables on attackers, leveraging their need to adapt as a vulnerability.


