The Internet of Things (IoT) has revolutionized the way we interact with the world around us. From smart homes and wearable devices to industrial automation and healthcare technologies, IoT devices are becoming increasingly integrated into our daily lives. However, this widespread adoption of IoT technologies also brings with it a host of security implications. As these devices become more prevalent, they present a growing target for cybercriminals, making the security of IoT devices a critical concern and IOT Penetration Testing demands is surging.
IoT devices are often resource-constrained and always connected, making them attractive targets for cyberattacks. These devices collect, transmit, and store vast amounts of data, some of which can be highly sensitive. A breach in an IoT device can lead to significant privacy violations and potential financial loss. Furthermore, as IoT devices become more integrated into critical infrastructure, the potential impact of these breaches becomes even more severe.
This is where IoT penetration testing comes into play. Penetration testing, or pentesting, is a method of evaluating the security of a computer system, network, or software application by simulating attacks from malicious entities. In the context of IoT, penetration testing involves assessing the security of the devices themselves, as well as the networks and services they are connected to. It’s a critical process that helps identify vulnerabilities before they can be exploited by attackers.
One of the methodologies that has been developed to guide this process is the PatrIoT methodology. PatrIoT, which stands for Practical and Agile Threat Research for IoT, is an academic research resulting on a comprehensive approach to IoT penetration testing. It was developed to address the unique challenges posed by IoT devices, which often differ significantly from traditional IT systems. The PatrIoT methodology is built on four key elements: logical attack surface decomposition, compilation of top 100 weaknesses, lightweight risk scoring, and step-by-step penetration testing guidelines.
This guide will provide a detailed walkthrough of the PatrIoT methodology, offering practical advice and insights for penetration testers looking to secure IoT devices. Whether you’re a seasoned cybersecurity professional or new to IoT penetration testing, this guide will provide the knowledge and IOT pentest tools you need to effectively assess and improve the security of IoT devices.
Understanding IoT Attack Surfaces
In the realm of IoT, understanding the various attack surfaces is crucial for effective penetration testing. Unlike traditional IT systems, IoT devices present a unique set of attack surfaces due to their diverse nature and the variety of ways they interact with the world. Here, we delve into the seven key attack surfaces in IoT: hardware, firmware, radio protocol, network service, web application, cloud API, and mobile app.
- Hardware: The physical components of an IoT device can be a target for attackers. This can include everything from the device’s circuit board to its USB ports. For instance, an attacker might exploit a hardware vulnerability to physically tamper with a device, potentially gaining access to sensitive data stored on the device or altering its functionality.
- Firmware: Firmware is the low-level software that controls the hardware of an IoT device. It’s often stored in the device’s read-only memory (ROM). Firmware vulnerabilities can allow an attacker to modify the device’s firmware, potentially giving them control over the device’s operations. For example, the infamous Mirai botnet exploited vulnerabilities in the firmware of IoT devices to create a massive botnet.
- Radio Protocol: Many IoT devices communicate using radio protocols such as Wi-Fi, Bluetooth, Zigbee, or Z-Wave. If these communications are not properly secured, an attacker could potentially intercept or alter them. For instance, an attacker might exploit a vulnerability in a device’s Bluetooth protocol to carry out a Man-in-the-Middle (MitM) attack, intercepting and potentially altering the device’s communications.
- Network Service: IoT devices often provide network services that can be accessed over a network. These services can be a target for attackers. For example, an attacker might exploit a vulnerability in a device’s network service to gain unauthorized access to the device or to launch a Denial-of-Service (DoS) attack.
- Web Application: Many IoT devices are controlled via web applications. These applications can present a variety of attack surfaces, including user interfaces, APIs, and server-side infrastructure. An attacker might, for example, exploit a Cross-Site Scripting (XSS) vulnerability in the web application controlling an IoT device to gain control over the device or access sensitive data.
- Cloud API: Many IoT devices interact with cloud-based services via APIs. If these APIs are not properly secured, an attacker could potentially gain access to sensitive data or control over the device. For instance, an attacker might exploit a vulnerability in a device’s cloud API to gain unauthorized access to user data stored in the cloud.
- Mobile App: Many IoT devices are controlled via mobile apps. These apps can present a variety of attack surfaces, including user interfaces, APIs, and local data storage. An attacker might, for example, exploit a vulnerability in the mobile app controlling an IoT device to gain control over the device or access sensitive data.
Understanding these attack surfaces and how they can be exploited is the first step in effective IoT penetration testing. By knowing where the vulnerabilities lie, penetration testers can better focus their efforts and develop more effective testing strategies.
Identifying IoT Weaknesses
Identifying potential weaknesses in IoT environments is a critical step in the penetration testing process. These weaknesses, often referred to as vulnerabilities, are the gaps or flaws in a system that can be exploited by attackers to gain unauthorized access or cause harm. Here, we’ll provide an overview of the top 100 weaknesses in IoT environments, explain how these weaknesses can be exploited, and discuss two important resources for understanding IoT vulnerabilities: the OWASP IoT Top 10 (OWASP IOTP) and the MITRE Common Weakness Enumeration (CWE).
The top 100 weaknesses in IoT environments cover a wide range of potential vulnerabilities. These can include everything from weak default credentials and insecure network services to outdated firmware and insecure cloud interfaces. Each of these weaknesses represents a potential entry point for an attacker, and understanding them is key to securing IoT devices:
- Weaknesses of IoT physical interfaces (link)
- Weaknesses of IoT firmware (link)
- Weaknesses of IoT network services (link)
- Weaknesses of IoT web application (link)
- Weaknesses of IoT cloud services (link)
- Weaknesses of IoT mobile application (link)
- Weaknesses of IoT radio communication (link)
For example, one common weakness in IoT devices is the use of weak or default credentials. Many IoT devices come with default usernames and passwords that are often easily guessable or publicly available. Attackers can exploit this weakness to gain unauthorized access to the device. Once inside, they can alter the device’s functionality, access sensitive data, or use the device as a launching point for further attacks.
Another common weakness is insecure network services. IoT devices often provide network services that can be accessed over a network. If these services are not properly secured, they can be exploited by attackers to gain unauthorized access to the device or to launch a Denial-of-Service (DoS) attack.
To help organizations understand and mitigate these weaknesses, several resources are available. The Open Web Application Security Project (OWASP) publishes a list of the top 10 most critical security risks to IoT devices. This list, known as the OWASP IoT Top 10, provides a starting point for organizations looking to secure their IoT devices.
Similarly, the MITRE Corporation maintains the Common Weakness Enumeration (CWE), a community-developed list of common software weaknesses. The CWE provides detailed descriptions of many common types of vulnerabilities, along with guidance on how to prevent them.
Understanding these weaknesses and how they can be exploited is a critical part of IoT penetration testing. By identifying potential vulnerabilities, penetration testers can help organizations secure their IoT devices and protect against potential attacks.
Risk Scoring and IoT Pentest
In the world of IoT penetration testing, understanding the potential risk associated with each identified vulnerability is crucial. This is where risk scoring comes into play. Risk scoring is a method used to quantify the potential impact of a vulnerability, taking into account factors such as the severity of the potential damage, the likelihood of the vulnerability being exploited, and the resources required to exploit it. In this section, we’ll introduce the concept of lightweight risk scoring, explain how to assess the risk of potential vulnerabilities, and provide examples of risk scoring for common IoT vulnerabilities.
The Common Vulnerability Scoring System (CVSS) as well as the OWASP provide a risk rating methodology respectfully based on 8 and 16 parameters. In the case of IOT, it may difficult the gauge the value of those parameters and devoting much effort to these calculations may not yield much information or may not pay off.
Lightweight risk scoring is a streamlined approach to risk assessment that aims to reduce the overhead of the process. Traditional risk scoring methods can be time-consuming and complex, requiring detailed knowledge of the system being tested and the potential threats it faces. Lightweight risk scoring, on the other hand, simplifies this process, making it more accessible and manageable, especially in environments with a large number of devices or vulnerabilities. The score is inspired by the DREAD threat modeling method and include three parameters:
- Impact: The (D)amage of DREAD
- Coverage: the (A)ffected Users of DREAD
- Simplicity: the (R)eproducibility, (E)xploitability, and (D)iscoverability of DREAD
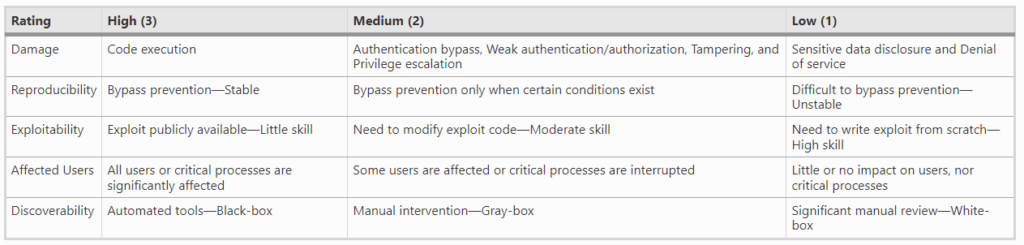
The penetration tester assigns a value between 1 and 3 to these three parameters, and giving the following risk rating equation
R = (impact+coverage+simplicity∗3)/5
The process of assessing the risk of potential vulnerabilities involves several steps.
- First, the severity of the potential damage caused by exploiting the vulnerability is assessed. This can include factors such as data loss, system downtime, and reputational damage.
- Next, the likelihood of the vulnerability being exploited is evaluated, taking into account factors such as the complexity of the exploit and the skills and resources required by an attacker.
- Finally, these factors are combined to produce a risk score, which can be used to prioritize remediation efforts.
For example, consider a vulnerability that allows an attacker to gain unauthorized access to an IoT device. If the device controls a critical system and contains sensitive data, the potential damage could be severe. If the vulnerability is easy to exploit and requires few resources, the likelihood of exploitation could be high. In this case, the risk score would be high, indicating that this vulnerability should be a high priority for remediation.
On the other hand, consider a vulnerability that allows an attacker to cause a minor disruption in a non-critical system. If the vulnerability is difficult to exploit and requires significant resources, the likelihood of exploitation could be low. In this case, the risk score would be low, indicating that this vulnerability is a lower priority for remediation.
By understanding the potential risks associated with each vulnerability and prioritizing them accordingly, organizations can more effectively allocate their resources and focus their efforts on the most critical vulnerabilities. This is the power of risk scoring in IoT penetration testing.
Step-by-Step IoT Penetration Testing Guidelines
The PatrIoT methodology provides a comprehensive, step-by-step guide to conducting IoT penetration testing. This approach ensures that all potential attack surfaces are considered and that the testing process is thorough and systematic. Here, we’ll provide a detailed walkthrough of these guidelines and explain how to apply the PatrIoT methodology in practice.
- Preparation: The first step in any penetration testing process is preparation. This involves gathering as much information as possible about the IoT device or system to be tested. This can include technical specifications, network diagrams, and any available documentation. This information will help you understand the device’s architecture and functionality, which is crucial for effective testing.
- Attack Surface Decomposition: Next, the IoT device or system is decomposed into its various attack surfaces. As discussed earlier, these can include hardware, firmware, radio protocol, network service, web application, cloud API, and mobile app. Each of these attack surfaces represents a potential entry point for an attacker, and each should be thoroughly tested.
- Threat Modeling and Risk Scoring: Once the attack surfaces have been identified, the next step is to model potential threats and score them based on their risk. This involves identifying potential vulnerabilities, assessing the potential damage they could cause, and the likelihood of them being exploited. This risk score will help prioritize testing efforts and focus on the most critical vulnerabilities.
- Penetration Testing: With the preparation complete, the actual testing can begin. This involves attempting to exploit the identified vulnerabilities to assess their potential impact. The specific techniques used will depend on the attack surface and the nature of the vulnerability. For example, testing a hardware attack surface might involve physical tampering with the device, while testing a network service might involve attempting to exploit a known vulnerability in the service.
- Reporting and Mitigation: The final step in the process is to report the findings and recommend mitigation strategies. This should include a detailed description of each vulnerability, the potential impact, and recommended mitigation strategies. It’s important to communicate these findings clearly and effectively to ensure that they are properly addressed.
To illustrate how this process works in practice, consider the following case study. A penetration tester is tasked with testing a smart home security system. They begin by gathering information about the system, including its technical specifications and network architecture. They then decompose the system into its various attack surfaces, which include the hardware of the security cameras, the firmware running on the cameras, the network services used to transmit video data, and the cloud API used to store and access the data.
The tester then models potential threats to each of these attack surfaces, identifying vulnerabilities such as weak default credentials, outdated firmware, insecure network services, and an insecure cloud API. They score each of these vulnerabilities based on their potential impact and the likelihood of exploitation, prioritizing the most critical vulnerabilities for testing.
The tester then conducts penetration testing, successfully exploiting several of the identified vulnerabilities. They document their findings, providing a detailed description of each vulnerability, the methods used to exploit them, and the potential impact. They then recommend mitigation strategies, such as updating the firmware, strengthening the default credentials, securing the network services, and securing the cloud API.
By following these step-by-step guidelines, the tester was able to conduct a thorough and effective penetration test of the smart home security system, identifying critical vulnerabilities and recommending strategies to mitigate them. This is the power of the PatrIoT methodology in practice.
Reporting and Mitigation for IOT Penetration Testing
Once the penetration testing process is complete, the next crucial step is to report the findings and propose mitigation strategies. This stage is vital as it provides the organization with the information necessary to address the identified vulnerabilities and enhance their IoT security.
Reporting Findings
The report should be clear, concise, and comprehensive, detailing each vulnerability discovered during the testing process. For each vulnerability, the report should include:
- A description of the vulnerability and the attack surface it affects
- The steps taken to exploit the vulnerability
- The potential impact if the vulnerability were to be exploited, including any data that could be compromised and the potential effects on the device’s functionality
- The risk score of the vulnerability, based on its potential impact and the likelihood of exploitation
The report should be structured in a way that is easy to understand, even for non-technical stakeholders. Visual aids, such as diagrams or screenshots, can be helpful in illustrating complex issues.
Mitigation Strategies
For each identified vulnerability, the report should also include recommended mitigation strategies. These recommendations should be practical, specific, and actionable, providing the organization with a clear path to address each vulnerability.
Mitigation strategies can vary widely depending on the nature of the vulnerability and the specific IoT device or system. They might include:
- Updating firmware or software to patch known vulnerabilities
- Strengthening authentication mechanisms, such as implementing stronger password policies or adding two-factor authentication
- Securing network services, such as implementing encryption for data in transit
- Hardening device configurations to reduce potential attack vectors
- Implementing intrusion detection systems to identify and respond to potential attacks
Ongoing Vulnerability Research and Testing
Finally, it’s important to emphasize that IoT security is not a one-time effort. New vulnerabilities can emerge as software is updated, new features are added, and attackers develop new techniques. Therefore, ongoing vulnerability research and regular penetration testing are crucial for maintaining the security of IoT devices and systems.
The organization should establish a regular schedule for penetration testing and vulnerability assessments. They should also stay informed about new vulnerabilities and threats in the IoT landscape, such as those documented in the OWASP IoT Top 10 and the MITRE CWE.
By effectively reporting the findings of an IoT penetration test, proposing practical mitigation strategies, and committing to ongoing vulnerability research and testing, organizations can significantly enhance the security of their IoT devices and systems.
Conclusion
As we navigate through the ever-evolving landscape of the Internet of Things, the importance of IoT penetration testing cannot be overstated. With an estimated 75 billion IoT devices expected to be in use by 2025, the potential attack surface for cybercriminals is vast. Each device, from smart home appliances to industrial sensors, represents a potential entry point for an attacker. Therefore, ensuring the security of these devices is not just a necessity, but a critical responsibility for all stakeholders involved.
Throughout this guide, we’ve explored the PatrIoT methodology, a comprehensive approach to IoT penetration testing. This methodology, with its focus on logical attack surface decomposition, compilation of top 100 weaknesses, lightweight risk scoring, and step-by-step penetration testing guidelines, provides a robust framework for identifying and addressing vulnerabilities in IoT devices and systems. It offers a systematic approach to understanding the unique challenges posed by IoT devices and provides practical strategies for securing them.
However, it’s important to remember that securing IoT devices is not a one-time effort. The landscape of IoT security is constantly changing, with new vulnerabilities emerging and old ones evolving. Therefore, continued learning and vigilance are crucial. Regular penetration testing, staying up-to-date with the latest research, and maintaining a proactive approach to security are all essential practices in this regard.
As we continue to embrace the convenience and benefits of IoT, let’s also commit to prioritizing its security. By doing so, we can ensure that the Internet of Things serves as a tool for progress, rather than a gateway for cyber threats. Whether you’re a seasoned cybersecurity professional or just starting your journey in IoT security, remember that every step taken towards securing an IoT device is a step towards a safer, more secure digital world.
Secure your IoT ecosystem with XRATOR’s comprehensive IoT Penetration Testing services. Our expert team uses the latest methodologies, including the PatrIoT approach, to identify vulnerabilities across all IoT attack surfaces. From hardware and firmware to cloud APIs and mobile apps, we provide thorough testing to ensure your IoT devices are resilient against cyber threats.


