Air-gapped networks are considered to be the safest of all. These networks are physically isolated from other systems and networks, making it difficult for hackers to penetrate them. However, a recent breakthrough in the world of cybersecurity has put air-gapped networks at risk. The COVID-bit attack is a new type of attack that enables the leaking of sensitive information from air-gapped systems to nearby receivers carried by a malicious person.
There have been several high-profile cases of air-gapped systems being targeted by malicious actors. For example the Stuxnet worm targeted the Iranian nuclear program in 2010. It was able to spread from a computer connected to the internet to an air-gapped network containing centrifuges that were being used to enrich uranium. The worm caused these centrifuges to spin out of control, effectively sabotaging the nuclear program.
Another example is Agent.BTZ, a piece of malware that targeted U.S. military networks in 2008. Allegedly used by the Turla advanced threat group, the malware was able to spread from a computer connected to the internet to air-gapped systems within the military network, allowing sensitive information to be exfiltrated.
What is COVID-Bit Attack?
A researcher has uncovered a new type of attack called COVID-Bit in a paper: “COVID-bit: Keep a Distance of (at least) 2m From My Air-Gap Computer!“. COVID-Bit is a novel attack that enables the leaking of sensitive information from air-gapped systems to nearby receivers carried by a malicious person. The attack works by exploiting modern computers’ dynamic power and voltage regulation and manipulating the loads on CPU cores. This manipulation generates electromagnetic radiation in specific low-frequency bands, which is then intercepted by a nearby receiver, such as a smartphone.
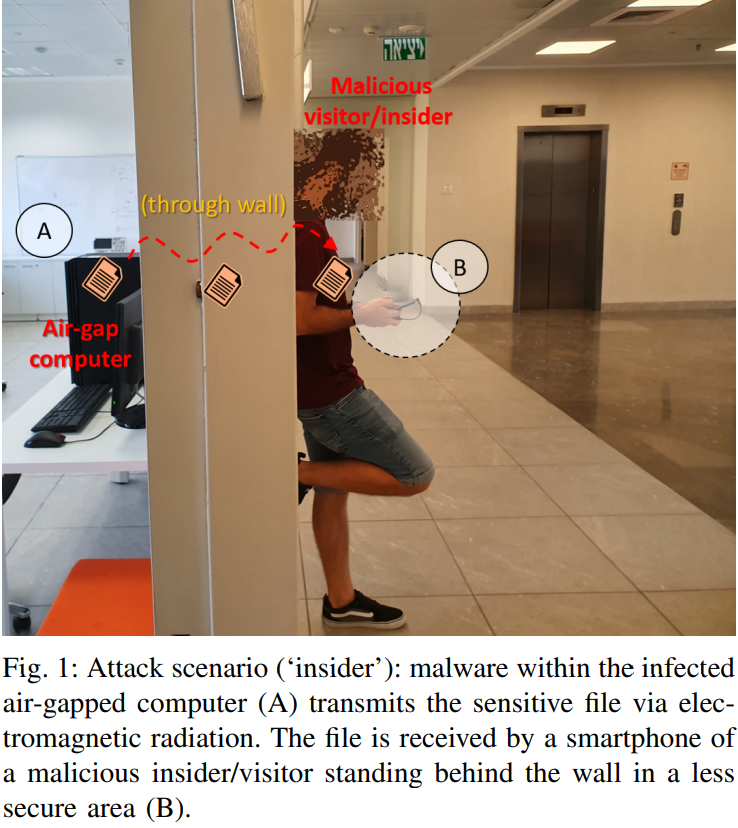 The COVID-bit attack can operate from a normal user-level process and even within a virtual machine (VM). The researchers who discovered this attack have successfully leaked information from air-gapped workstations to nearby receivers at a bandwidth of 1000 bits/sec. This is a significant discovery that poses a serious threat to the security of air-gapped networks.
The COVID-bit attack can operate from a normal user-level process and even within a virtual machine (VM). The researchers who discovered this attack have successfully leaked information from air-gapped workstations to nearby receivers at a bandwidth of 1000 bits/sec. This is a significant discovery that poses a serious threat to the security of air-gapped networks.
Risks and Threats of Air-Gapped Bypass
To understand the gravity of the situation, let’s take a closer look at how air-gapped networks work and why they were considered to be the safest of all. Air-gapped networks are physically isolated from other systems and networks, meaning that they do not have any direct connections to the internet or other networks. This makes it difficult for hackers to penetrate these networks, as they cannot access them remotely.
However, with the COVID-bit attack, hackers can now target air-gapped networks by physically being near the target system. They can carry a nearby receiver, such as a smartphone, and use it to intercept sensitive information that is encoded in low-frequency electromagnetic radiation. This puts the security of air-gapped networks at risk, as they are now vulnerable to physical attacks.
Protecting Against COVID-Bit Attacks
So, what can be done to protect air-gapped networks from the COVID-bit attack? There are several countermeasures that can be put in place to reduce the risk of a successful attack. These include hardware-based solutions, such as external electromagnetic receivers that persistently monitor the relevant spectrum of 0 – 60 kHz. Another hardware-based solution is to use a radio frequency jamming system to block the reception or transmission of signals in the relevant frequency bands of 0 – 60 kHz.
However, these solutions are not foolproof, as malicious insiders and implanted hardware can still compromise the security of air-gapped networks. In such cases, physical security measures such as Faraday shielding can be used to prevent electromagnetic emissions from the computer systems. This approach involves encasing the entire system in a thin layer of conductive material or metal mesh.
Conclusion
COVID-Bit is a new and dangerous threat to air-gapped networks, and it is essential that organizations take steps to protect themselves against this type of attack. While there are countermeasures that can be put in place, such as using external electromagnetic receivers or radio jamming systems, it is important to understand that no solution is foolproof. The only way to ensure the security of sensitive information is to implement multiple layers of security and to stay vigilant against new threats like COVID-Bit.