When CloudSEK researchers revealed that over 18,000 wannabe hackers had been compromised through a trojanized malware builder, the cybersecurity community’s reaction was predictably amused. The irony of hackers getting hacked makes for great headlines. But beneath this surface-level schadenfreude lies a more fascinating strategic reality: we may be witnessing a large criminal intelligence gathering operations, like a very few documented in the public domain.
Beyond the Obvious
The scale alone should give us pause. 18,459 compromised devices isn’t just a successful malware campaign. The geographical distribution reads like a who’s who of cybercrime hotspots: Russia, United States, India, Ukraine, and Turkey. May it be methodical intelligence gathering on the cybercrime ecosystem itself?
Consider what the attackers gained access to: Discord tokens, browser data, keystrokes, and screenshots from thousands of aspiring cybercriminals. This isn’t just about compromising individual “script kiddies” – it’s about mapping the entry points, communication channels, and recruitment pathways of the broader criminal underground.
The inclusion of a kill switch is particularly telling. As we’ve seen with sophisticated actors like Turla or the Predator spyware operators, the ability to quickly terminate operations is a hallmark of strategic thinking. But while those groups focus on protecting their high-end infrastructure, this operation shows a different kind of operational security – one focused on intelligence gathering with a clean exit strategy.
The Clues of Criminal Intelligence in Practice
What makes this operation particularly clever is its targeting of the cybercrime ecosystem’s most vulnerable and verbose participants. New cybercriminals, eager to prove themselves, often:
- Share more operational details than seasoned criminals
- Connect their criminal activities to their regular online presence
- Maintain poor operational security practices
- Network actively with other aspiring criminals
By compromising these entry-level actors, the attackers gained visibility into:
- Emerging cybercrime trends and techniques
- Criminal recruitment and training channels
- Underground marketplace dynamics
- Potential law enforcement operations
The criminal underground is an intelligence goldmine. Every wannabe hacker searching for free tools, every amateur trying to make a name for themselves, represents a potential intelligence-gathering opportunity.
Exploring the Intelligence Operation Hypothesis
When we analyze this attack through an intelligence collection framework, what emerges is a potential carefully crafted intelligence operation that reveals mature understanding of both technical and human intelligence gathering.
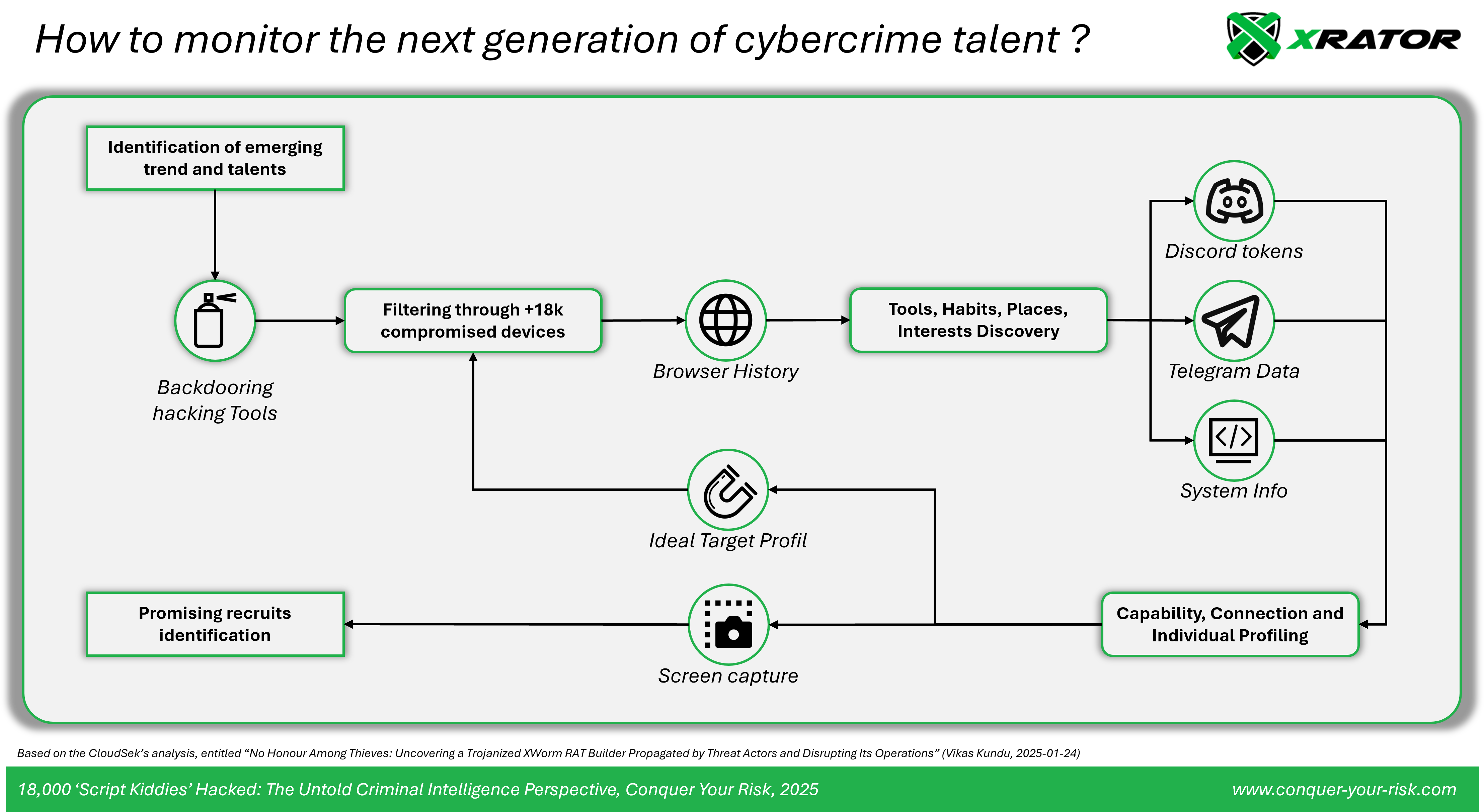
Direction: mapping the cybercrime ecosystem’s entry points
The operation began with precise requirements definition focused on mapping the cybercrime ecosystem’s entry points. By targeting aspiring cybercriminals, the actors positioned themselves to understand individual actors, and the entire recruitment and development pipeline of new criminal talent.
The collection planning demonstrates clean sophistication in the way it builds comprehensive profiles of aspiring cybercriminals. Consider the seemingly straightforward collection of Discord tokens and browser data – this combination allows operators to :
- map both the public and private communications of targets,
- understand how they operate in their daily online lives,
- draw a social network of the individuals target.
Screenshot collection enables the mapping of tools, techniques, and procedures these new actors are learning and attempting to deploy.
Source Development : valuables for free
The source development strategy leverages understanding of how new cybercriminals enter the ecosystem. The initial entry typically occurs through tutorial-seeking behavior – aspiring criminals search YouTube, GitHub, and forums for “free” tools and learning resources. This creates predictable patterns of behavior that sophisticated actors can exploit. What’s particularly telling is how the operation exploited a key psychological vulnerability: new cybercriminals want sophisticated tools but lack the resources or connections to acquire them legitimately. The promise of a “free XWorm RAT builder” plays directly into this desire. The fact that the operation sustained itself across multiple distribution channels – from GitHub to Telegram to specialized forums – suggests deep understanding of how aspirants move through these spaces as they develop their capabilities.
By embedding their trojanized builder in GitHub repositories, YouTube tutorials, and Telegram channels, they positioned themselves at the exact points where aspiring criminals take their first steps into operational activity. This placement provides continuous intelligence about new trends, tools, and techniques being adopted at the ground level.
The geographic distribution adds another layer to our theory. The top affected countries (Russia, USA, India, Ukraine, Turkey) align with known cybercrime ecosystem entry points – regions with high technical literacy but varying levels of law enforcement pressure. This suggests the operators understood not just technical entry points, but cultural and geographical patterns in cybercrime recruitment.
Collection, Processing and Exploitation : down the funnel
By collecting and categorizing different types of data, the operators built comprehensive profiles of the cybercrime ecosystem’s newest entrants. Browser data reveals research patterns and learning pathways. Discord tokens expose communication networks and potential recruitment channels. Screenshots capture operational security mistakes and technical capabilities. Together, this creates a detailed map of how new criminals develop their skills and build their networks.
The selective exploitation pattern (only 2,068 out of 18,459 devices targeted for credential theft) becomes more significant in this context. It suggests the operators were identifying and profiling specific types of new entrants – possibly those showing particular aptitude or connecting to existing criminal networks, as evidenced by the Discord token collection focusing on communication patterns. The selective targeting suggests careful curation of high-value targets. An ordinary cybercrime operation would likely have attempted to monetize all compromised systems. Instead, this operation showed the hallmarks of patient, strategic intelligence collection.
The Strategic Intelligence Value
The real power of this operation lies in how these different intelligence streams combine to create actionable insights. Starting with indiscriminate engagement, browser histories and screenshots together reveal which tutorials and tools aspiring criminals find most useful, allowing sophisticated actors to better understand potential attack vectors. Discord tokens combined with system information create detailed profiles of individual actors, their capabilities, and their connections – valuable for both tracking emerging threats and potentially recruiting talented operators.
The geographic distribution of compromised systems – concentrated in Russia, USA, India, Ukraine, and Turkey – provides strategic insight into cybercrime talent pools and potential intelligence source recruitment grounds. When combined with the selective targeting of credential theft, this suggests the operators were mapping not just individual actors, but entire regional cybercrime ecosystems.
This comprehensive intelligence gathering creates multiple strategic advantages. Beyond the immediate value of understanding emerging threats, it provides insight into cybercrime talent development, enables the identification of promising recruits, and maps the communication channels and tools that form the backbone of the criminal underground.
Confidence Assessment
Our analysis of this operation yields three primary hypotheses, each with distinct implications for understanding the true nature of this campaign. We assess with high confidence that this represents a an intelligence operation. The elimination of both law enforcement and cybercrime hypotheses, combined with the sophisticated intelligence gathering patterns, creates a compelling case.
(Primary) Criminal Intelligence Operation
The strongest evidence supporting a criminal intelligence operation emerges from the selective exploitation pattern. With only 2,068 devices targeted for deep credential theft out of 18,459 infected systems, we see behavior inconsistent with typical cybercrime motivation. This targeting aligns with intelligence gathering aimed at understanding specific segments of the cybercrime ecosystem.
The geographic distribution across Russia, USA, India, Ukraine, and Turkey suggests systematic mapping of cybercrime talent pools rather than opportunistic infection. When combined with the sophisticated data categorization – separating screenshots, browser data, and communication tokens – we see a pattern of professional intelligence collection.
The public exposure through security research presents a significant contracting factor. Sophisticated intelligence operations typically maintain longer periods of stealth. The use of common criminal infrastructure like Telegram also introduces uncertainty, though this could represent intentional blending with the target environment. Also the presence of the kill switch represents operational security measures typical of intelligence collection : the ability to quickly terminate compromised assets if the operation risks exposure.
(Secondary) Advanced Cybercrime Operation
An alternative interpretation views this as an evolution of traditional cybercrime. The focus on credential theft and use of familiar criminal infrastructure supports this view. Yet the limited financial exploitation despite significant access contradicts typical cybercrime patterns. Typical cybercrime operations aggressively monetize their access – the restraint shown here suggests different motivations.
The sophisticated operational security measures, including virtualization detection and selective targeting, indicate capabilities and patience compatible with advanced criminal groups. Most notably, the methodical collection of communication data and system profiling suggests strategic intelligence gathering rather than immediate financial exploitation.
But the investment in sophisticated distribution channels and long-term monitoring capabilities would represent significant overhead for a criminal operation without clear financial return. This level of infrastructure development and maintenance, combined with limited monetization, strongly suggests objectives beyond traditional cybercrime profit models.
(Tertiary) Law Enforcement Operation
The indiscriminate initial infection of over 18,000 devices fundamentally conflicts with law enforcement’s legal and operational constraints around targeted surveillance and evidence collection. The geographic spread across Russia, USA, India, Ukraine, and Turkey creates jurisdictional complexity that would make legitimate law enforcement action nearly impossible. No existing law enforcement coalition could effectively operate across these boundaries for low-level targets. Most tellingly, the operation’s focus on aspiring cybercriminals – essentially script kiddies learning their craft – contradicts law enforcement prioritization. Law enforcement agencies, with limited resources, typically target established threats causing significant societal harm like ransomware operators or major cybercrime groups. Expending resources to track thousands of novice actors experimenting with free tools would represent a misallocation of law enforcement capabilities and mandate.
Conclusion
The operation’s scale and methodology perfectly align with intelligence collection requirements. The initial wide-net approach, followed by selective deep exploitation of specific targets, mirrors classic intelligence filtering techniques. The comprehensive data collection – from communication tokens to screenshots to system profiles – creates multi-dimensional intelligence value that goes far beyond simple credential theft or criminal prosecution objectives.
The geographic spread across major cybercrime hubs (Russia, USA, India, Ukraine, Turkey) suggests an operation designed to map global talent development in the cybercrime ecosystem. This broad international scope, while problematic for law enforcement operations, aligns perfectly with intelligence gathering objectives focused on understanding criminal talent pipelines and recruitment patterns.
Our previous uncertainty about operational exposure requires revision. The public discovery through security research, rather than undermining the intelligence operation hypothesis, might represent an acceptable operational risk given the value of the intelligence gathered. The use of common criminal infrastructure like Telegram, similarly, can be better understood as intentional blending with the target environment rather than a limitation.
The systematic focus on aspiring cybercriminals – mapping their learning pathways, tools, and communications – represents perhaps the strongest indicator of intelligence objectives. This population, while of limited interest to law enforcement and insufficient value for cybercrime operations, provides crucial insight into the evolution and future capabilities of the criminal ecosystem.
The operation’s sophisticated combination of technical capabilities with deep understanding of criminal ecosystem entry points pushes our assessment from medium-high to high confidence. Neither cybercrime groups nor law enforcement agencies have demonstrated similar capabilities or strategic patience in targeting the developmental pipeline of criminal talent.


