In today’s cybersecurity world, new vulnerabilities are found and exploited every day. To stay protected, it’s essential to have a vulnerability management program that focuses on the most critical threats to your business.
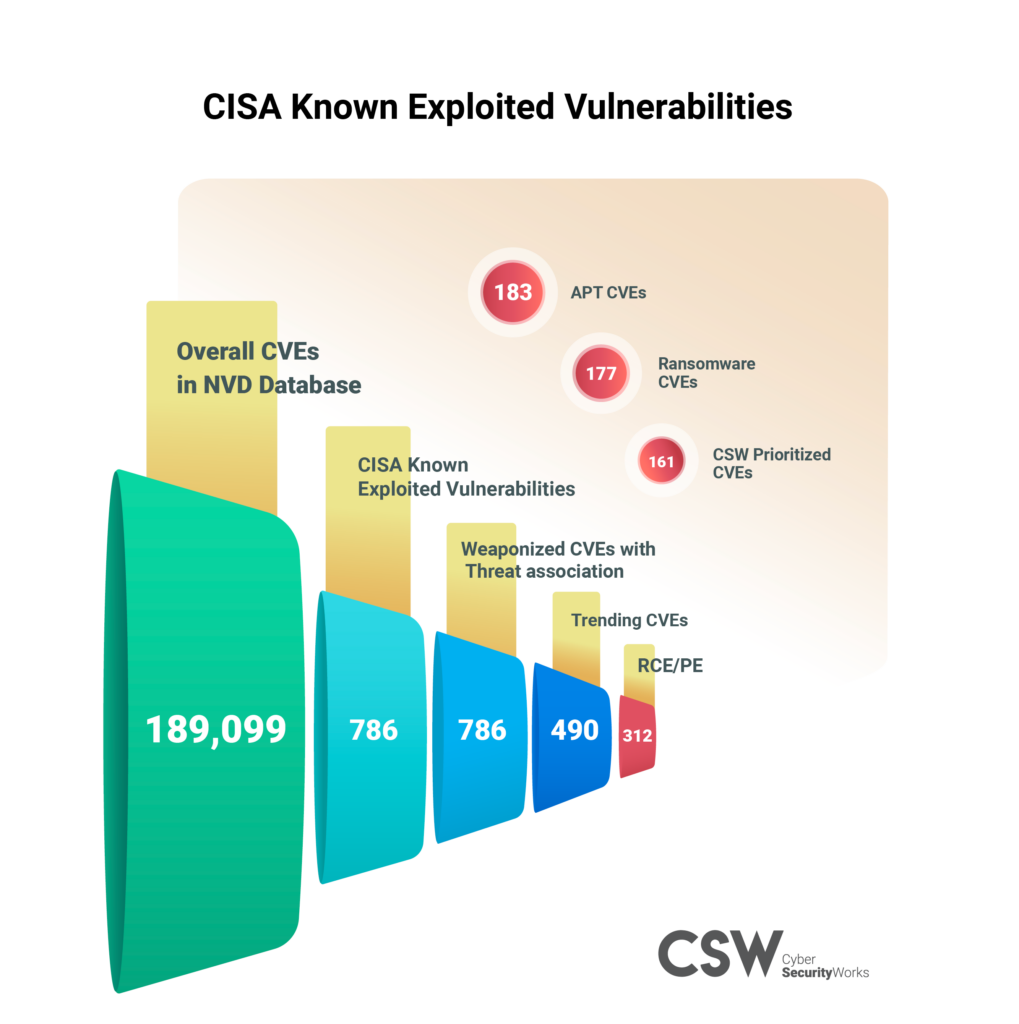 This blog post will show you how to prioritize which vulnerabilities to fix first, using data to guide you. We’ll explain risk scoring and how to calculate it, with a focus on the Exploit Prediction Scoring System (EPSS) model. Our goal is to help you identify and address the most serious vulnerabilities specific to your business, so you can stay secure.
This blog post will show you how to prioritize which vulnerabilities to fix first, using data to guide you. We’ll explain risk scoring and how to calculate it, with a focus on the Exploit Prediction Scoring System (EPSS) model. Our goal is to help you identify and address the most serious vulnerabilities specific to your business, so you can stay secure.
Understanding Risk Scoring for Effective Cybersecurity
Risk scoring evaluates and quantifies the levels of cyber risk associated with vulnerabilities in an organization’s IT infrastructure. This method is crucial for vulnerability management programs, helping organizations prioritize which vulnerabilities to fix first. With potentially thousands of vulnerabilities, it’s impractical to address them all, making risk scoring essential.
Risk scoring involves assigning a value or score to each vulnerability, considering factors such as the potential impact on the organization, the likelihood of a threat occurring, and the criticality of the vulnerability.
To identify these vulnerabilities, we use the CVE (Common Vulnerabilities and Exposures) system. This system standardizes the names of publicly known vulnerabilities and security issues found in software and hardware products. Each CVE corresponds to a specific security vulnerability and is assigned a unique identifier known as a CVE ID (e.g., CVE-2024-3094). This identifier is widely used in the cybersecurity industry by security researchers, vendors, and organizations to reference and track vulnerabilities.
For each CVE, we assign a risk score, which can be represented with the following formula:
Risk = Vulnerability x Information Value (Impact) x Threat
Today, most vulnerability management platforms and cybersecurity experts rely solely on the CVSS (Common Vulnerability Scoring System) to manage and prioritize vulnerabilities. Or they go south by using deprecated frequency based complex quantification model, that at the end of the day are disconnected from reality. To enhance your risk scoring, you should incorporate the EPSS (Exploit Prediction Scoring System) score and BIA (Business Impact Analysis). To achieve coherent risk scoring results, it’s crucial to select the right data to represent the vulnerability, the threat, and the information values (impact).
Enhancing Vulnerability Scoring with Contextual Insights
To represent the vulnerability score of a CVE (Common Vulnerabilities and Exposures), the standard is to use the CVSS (Common Vulnerability Scoring System) score. The CVSS is a standardized method widely used in cybersecurity to assess the severity and exploitability of vulnerabilities for each CVE.
The CVSS provides a numerical score ranging from 0 to 10 based on various metrics such as attack vector, impact, and complexity of exploitation. This score is a valuable quantitative representation of the vulnerability, and it’s the way to go in cybersecurity management software to prioritize patching and mitigation efforts. For more details on calculating the CVSS score, you can use and test the CVSS calculator.
However, relying solely on the CVSS score has limitations. While it considers the impact on the confidentiality, integrity, and availability of data on a specific asset, it does not account for the context of these assets within the organization.
For example, a CVE with a CVSS score of 10/10 on a disconnected printer versus the CEO’s laptop would have vastly different potential business impacts. This discrepancy highlights the need to quantify the context in which a CVE exists and the type of assets affected.
So, how do we quantify the context where a CVE is or on what type of assets?
Incorporating Business Impact Analysis (BIA) for Contextual Risk Scoring
To quantify the context and impact of exploiting a vulnerability on the business, we use the Business Impact Analysis (BIA). The BIA is a structured process to assess the potential impact of disruptions on critical business functions or assets. It helps identify and prioritize risks to ensure business continuity and effective risk management strategies.
Here are the four key steps of a simplified BIA analysis:
- Identify Business Assets: Determine the key business assets or functions within the organization. For an e-commerce business, these could include website operations, product management, order processing, customer support, and logistics.
- Identify Feared Events: Identify potential disruptive events or incidents that could impact each business asset. These could include cyberattacks (e.g., DDoS attacks, data breaches), technical failures (e.g., server outages, payment gateway failures), logistical challenges (e.g., shipping delays), and other relevant threats.
- List Impacts: For each feared event, list the potential impacts or consequences on the corresponding business asset. Consider factors such as financial loss, operational disruption, customer dissatisfaction, reputational damage, and legal implications.
- Rate Severity: Rate the severity of impact for each feared event and business asset on a scale from 1 to 4, with 1 being low severity and 4 being high severity. This rating reflects the perceived magnitude of the impact on the business asset if the feared event were to occur.
To illustrate this process, let’s conduct a BIA for an online store:

In this example BIA, the severity score for the Customer Support asset is 2, while for Product Management it is 4. This means that the impact of an exploited vulnerability will vary significantly depending on the business asset affected.
Next, we need to determine which vulnerabilities are more likely to be exploited by an attacker.
Threat x Vulnerability : Integrating Exploit Prediction Scoring System (EPSS)
To assess the threat of a vulnerability being exploited, we use the Exploit Prediction Scoring System (EPSS). This machine learning model predicts the likelihood of a CVE being exploited in the wild within the next 30 days. Unlike traditional scoring systems, EPSS is updated daily to reflect the evolving threat landscape.
EPSS derives its score from various factors, including the characteristics of the vulnerability, the availability of exploit code, and the prevalence of the vulnerability in the wild. By providing a probability score, it offers a quantitative measure of the risk associated with each vulnerability, enabling organizations to make informed decisions about mitigation strategies.
The EPSS model provides each CVE with a percentile and an EPSS score. The EPSS score indicates the likelihood of the CVE being exploited in the next 30 days, while the percentile ranks the CVE’s EPSS score against all other CVEs, showing the percentage of CVEs with a lower EPSS score.
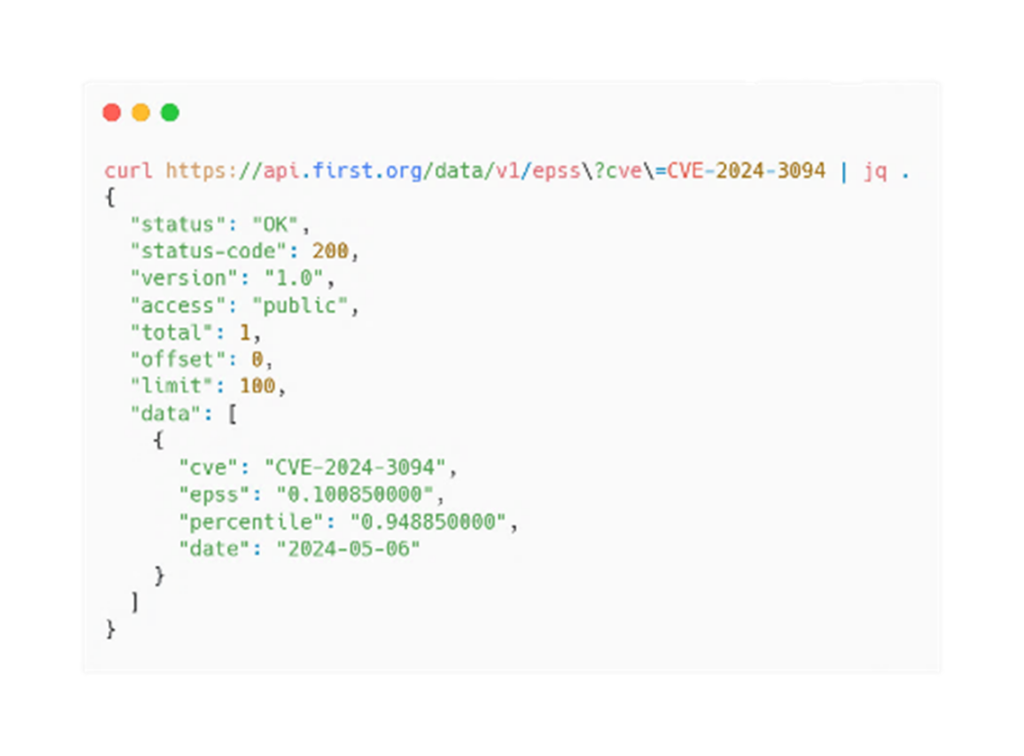
For example according to the official API, for CVE-2024-3094, the EPSS score on May 6, 2024, is 0.10085, indicating a 10% chance of exploitation within the next 30 days. The percentile is 0.94885, meaning this CVE is in the top 6% of most likely exploited CVEs. Below is an API data format for CVE-2024-3094, showing how the EPSS score changes over time.
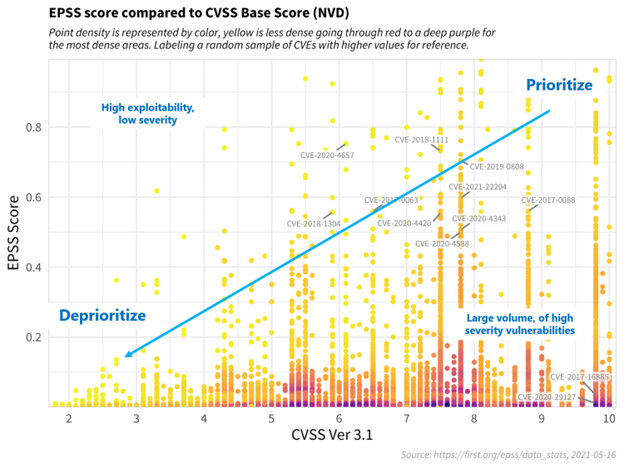
A graphical representation of all CVEs with their CVSS and EPSS scores highlights the most critical vulnerabilities. In the top-right corner, the CVEs to prioritize for patching are visible, while the numerous points (CVEs) at the bottom of the graph demonstrate why relying solely on the CVSS score is insufficient.
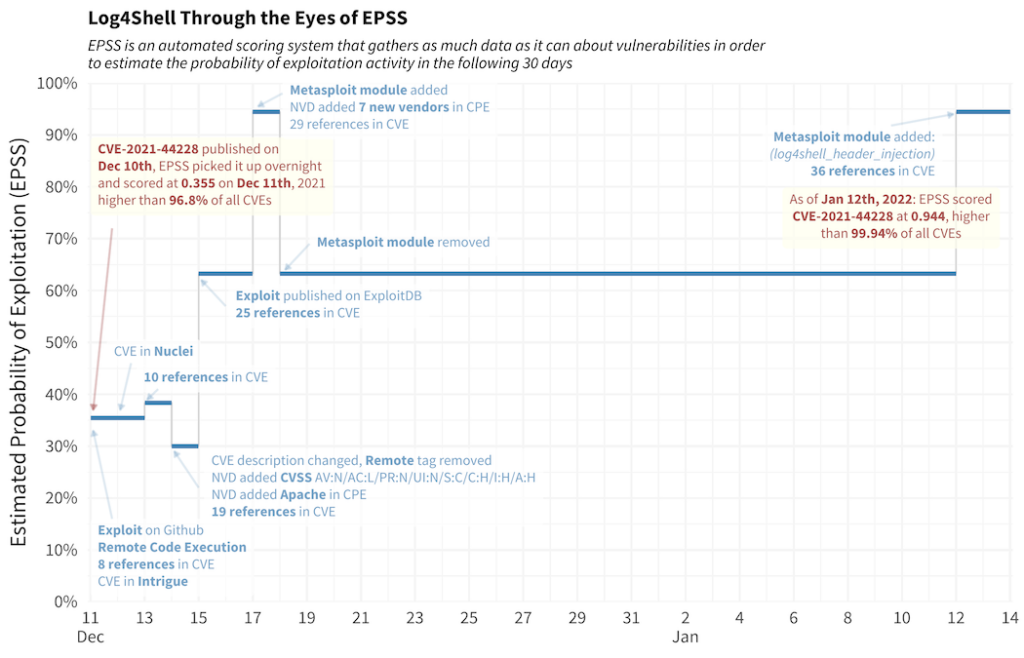
Most vulnerability management tools today only use the CVSS score. However, EPSS’s dynamic nature, adjusting scores based on daily events, is crucial for staying updated on the threat landscape. The case study of CVE Log4Shell illustrates how the EPSS score evolves as new information becomes available.
Integrating EPSS scores (threat) and business impact (BIA) into the existing CVSS score used in today’s vulnerability management tools can provide a more comprehensive risk assessment. So how to add the EPSS score (the threat) and the business impact (BIA) into the CVSS score already used in today’s vulnerability management tool?
Usecase : Combine EPSS and BIA for Risk Scoring and Vulnerability Prioritization
To illustrate the benefits of risk scoring in a vulnerability management program, we’ll apply the risk scoring formula to two vulnerabilities in our hypothetical e-commerce business. We identified two vulnerabilities: CVE-2014-0605 on the Customer Support Business Asset and CVE-2023-4966 on the Product Management Business Asset.
Most vulnerability management tools prioritize CVEs using only the CVSS score. CVE-2014-0605 has a CVSS score of 10/10, and CVE-2023-4966 has a CVSS score of 9.4/10. Based solely on the CVSS scores, CVE-2014-0605 would be patched first.
However, let’s apply the “true” risk score formula:
Risk = Vulnerability x Information Value (Impact) x Threat
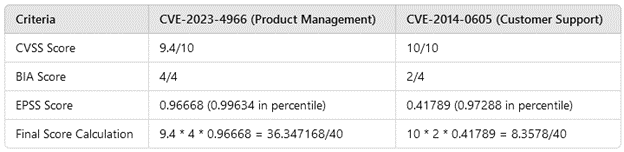
By applying the comprehensive risk score, the prioritization changes significantly compared to using just the CVSS score. This example demonstrates why it’s crucial to use risk scoring properly to identify critical vulnerabilities instead of relying solely on the CVSS score.
Disclaimer: To use the risk score effectively, it must be recalculated daily to reflect updates in the EPSS score.
Conclusion
Risk scoring is vital for an effective vulnerability management program. By integrating CVSS, BIA, and EPSS scores, organizations can prioritize vulnerabilities based on their unique context and the changing threat landscape. This comprehensive approach ensures that resources are used efficiently, focusing on the most critical vulnerabilities first, thereby strengthening the organization’s overall security posture. As threats evolve, it’s essential to continually update and refine risk scoring models to stay ahead and maintain strong cybersecurity defenses.
Discover how XRATOR apply this in real-time and at scale with XRATOR Operator.


