Governments, technology companies, researchers, and platforms do not possess a unified approach to inspect the various types of cyber infractions due to the fact that each of these entities have different objectives, resources, and regulations. Governments have limited resources to investigate cyber infractions and are often focused on high-profile cases that have the potential to affect national security or the public’s safety.
Technology companies, on the other hand, focus on protecting their own networks and customers, as well as addressing any legal or regulatory issues associated with cybersecurity. Researchers often focus on identifying new threats and vulnerabilities, while platforms are typically focused on protecting their users from malicious content. As a result, each of these entities has its own approach to inspecting cyber disruptions, leading to a lack of unified approach.
To address the issue, Meta has come up with its own Online Operations Kill Chain disclosed on November 2022 at the CyberWarCon conference. This tool is intended to be adapted to a variety of online activities. It outlines the phases a threat actor must go through to gain access to the internet, hide their presence, study and interact with their victims, and remain in place despite counter measure from defender. Meta Security Team use it to compare online operations, spot weaknesses that can be used, and single out the most essential possibilities for disruption over a broad range of dangers so that our security personnel do not work in isolation.
 What is the Origin of the Kill Chain in Cybersecurity ?
What is the Origin of the Kill Chain in Cybersecurity ?
The Intrusion Kill Chain is a cybersecurity concept that was first introduced by Lockheed Martin that identifies the seven steps of an attack and helps organizations defend against them. It was describes in the paper “Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains”. The seven steps of the kill chain are:
- Reconnaissance: gathering information necessary to conduct the operation,
- Weaponization: to combine malicious code with legitimate materials,
- Delivery: to transport the malicious payload into the target’s network,
- Exploitation: to leverage target’s weaknesses to execute the malicious payload,
- Installation: to install the malicious payload on a target’s host and ensure persistence,
- Command and control: to create a channel communication between the adversary’s network and the infected network,
- Actions on objectives: to perform the ultimate goal of the adversary.
By understanding the different stages of an attack, organizations can be better prepared to counter them.
The Kill Chain in Cybersecurity is an adaptation of the F2T2EA military’s kill chain. The F2T2EA stands for Find, Fix, Track, Target, Engage and Assess. This model is used to identify and stop enemy activity in a step-by-step approach. It covers activities that occur outside and within the defended network, making it a more comprehensive approach than the traditional cyber hygiene frameworks.
The cyber kill chain has known limitations, such as its insufficient capability of tracing host attack behaviors. Additionally, critics of the model point out that it is overly focused on the defensive side of security and does not provide sufficient guidance on how to respond to and recover from an attack. Additionally, it is too focused on network security and prevention of malware, and does not adequately address other attack vectors, such as social engineering or insider threats.
Why is Meta’s Online Operation Kill Chain Different ?
While Lockheed Martin Intrusion Kill Chain depict a rigid linear scenario, Meta’s cyber kill chain is modular and not only focused on malware-based cyber attacks. Meta has taken this kill chain framework and applied it to cyber espionage, influence operations, and other security threats. They created this framework with the open-source community in mind due to the rising number of online threats types.
Through the use of a common language and threat taxonomy, cyber defenders can gain a better understanding of the threat landscape and identify discrepancies in our collective protection. Doing so will create an extra layer of security, making it harder for malicious actors to carry out their operations online.
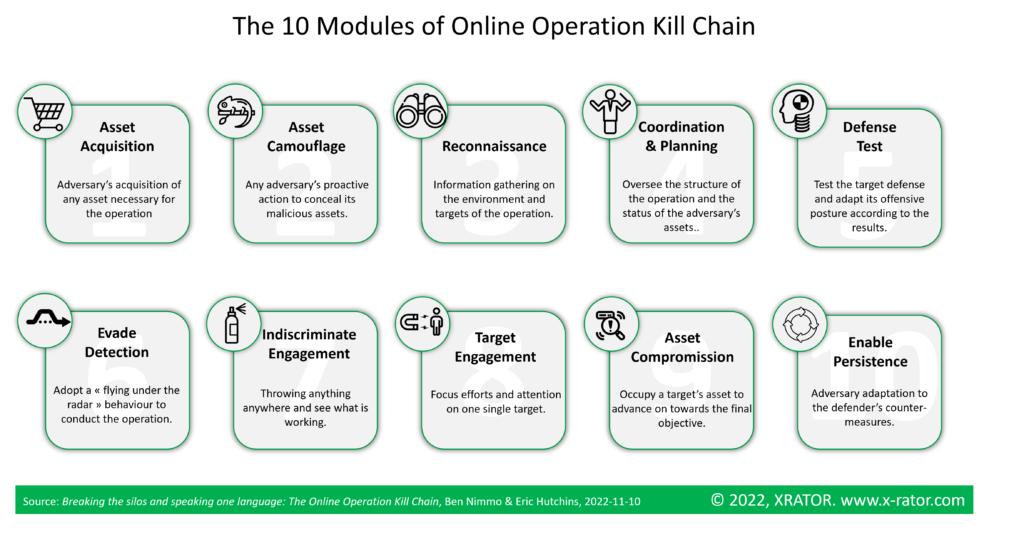
The tens modules that compose the Online Operation Kill Chain, mapped to MITRE ATT&CK, are the following:
- Asset Acquisition: Create, purchase or compromise resources necessary to conduct the online operation (MITRE ATT&CK Resource Development Tactic, TA0042),
- Asset camouflage: The measures taken by the adversary to let’s look like all its malicious asset legitimate (This module is no more in MITRE ATT&CK (Deprecated tactic Adversary OPSEC, TA0021), but similar to the Military Deception – MILDEC- tactic of Camouflage, a long-term and passive type of concealment),
- Reconnaissance: Active and passive, open-source and closed-source, information gathering on the target’s organization, individuals and technologies to support the coordination & planning of the operation (MITRE ATT&CK Reconnaissance Tactic, TA0043),
- Coordination & Planning: Managing the entire operation effort, from identifying the need for data to delivering finished intelligence that supports decision-making and action. This involves formulating specific collection, processing, analysis, and dissemination requirements. (This module is no more in MITRE ATT&CK (Deprecated tactics Priority Definition Planning, TA0012; and Priority Definition Direction, TA0013), but similar to the first step of the Intelligence Cycle),
- Defense Test: Testing capabilities externally to adjust the development objectives and the operational needs. (This module is no more in MITRE ATT&CK (Deprecated tactic Test Capabilities,TA0025)),
- Evade detection: All the techniques allowing to avoid detection of malicious artifacts and adversary’s behavior during the course of the operation (MITRE ATT&CK Defense Evasion, TA0005),
- Indiscriminate engagement: A type of engagement where you through all you have to the target (This module is not in MITRE ATT&CK, that focus on targeted attacks. It can be view as massive phishing campaign, mass credential harvesting or the auto-exploitation module of metasploit),
- Target engagement: A type of engagement where you focus on a single final target (This module is not in MITRE ATT&CK, that focus only on this type of engagement),
- Asset compromise: The adversary is gaining a foothold on a target’s asset (MITRE ATT&CK Initial Access Tactic, TA0001; but may also include the results of MITRE ATT&CK Lateral Movement Tactic, TA0008),
- Enable Persistence: The adversary is preparing to and adapting to defender security measures and intrusion counter-measures (MITRE ATT&CK Persistence tactic, TA0003; but may also include some reactive measures of MITRE ATT&CK Defense Evasion Tactic, TA0005; such as the MITRE ATT&CK Impair Defense technique (T1562) or MITRE ATT&CK Indicator Removal technique (T1070)).
Meta’s Online Operation Kill Chain and MITRE ATT&CK can be combined by using the ATT&CK framework to identify and understand the tactics, techniques and procedures used by attackers, and combining that with the Online Operation Kill Chain’s step-by-step process to identify, monitor, and respond to attacks. This allows organizations to gain a better understanding of the entire attack process, from initial reconnaissance to the post-attack cleanup. Additionally, the Online Operation Kill Chain can be used to identify gaps and opportunities in an organization’s current security posture.
Conclusion
Cyberdefenders protect computer systems, networks, and devices from cyber threats such as malware infections, scams, influence operations, and propaganda. All of these threats can have serious consequences for individuals and organizations, and it is important for cyberdefense to address all of them in order to provide comprehensive protection.
Malware infections, such as ransomware, can cause damage to systems and disrupt operations. Scams and influence operations, on the other hand, can be used to manipulate individuals and organizations, potentially leading to financial loss or damage to reputation. Propaganda can be used to spread misinformation or manipulate public opinion, and it is important for cyberdefense to be able to identify and respond to these efforts in order to protect against their potentially harmful effects.
By addressing all of these threats, cyberdefense can help to ensure the security and integrity of computer systems and networks, and protect against a wide range of potential harm. They also position on not just protecting technologies but the full organization and their value chain.


 What is the Origin of the Kill Chain in Cybersecurity ?
What is the Origin of the Kill Chain in Cybersecurity ?