In 2019, Carnegie Mellon University’s Software Engineering Institute (SEI) joined together with the Cybersecurity and Infrastructure Security Agency (CISA) to create the Stakeholder-Specific Vulnerability Categorization (SSVC) system. This system was designed to evaluate cyber vulnerabilities based on their threat level, potential for harm, and how widely the affected product is used.
By 2020, CISA had developed their own customized version of the SSVC decision tree to assess the vulnerabilities relevant to the United States government, state, local, tribal, and territorial governments (SLTT). Critical infrastructure entities are also concerned. As CVE and CVSS are not a good strategy enough, implementing the SSVC helps to better manage their vulnerability response and communication to the public.
Three Key Challenges in Vulnerability Management
Given the current risk landscape, companies of all sizes are faced with the task of controlling the amount and complexity of the system’s weaknesses. Enterprises with advanced vulnerability management systems attempt to find more effective methods for triage and prioritization. Smaller companies have difficulty knowing where to begin and how to allot limited funds. Fortunately, there is a way to automate vulnerability management and prioritize it more effectively. SEI and CISA have laid out three key steps to progress the vulnerability management system:
- Automation: Their is a critical need to improve automated Vulnerability Analysis and Vulnerability Exchange by relying on structured language such as Common Security Advisory Framework (CSAF).
- Assessment: One vulnerability will not impact the same way each organization, but tool for decision-making such as the Vulnerability Exploitability eXchange (VEX) have no widespread adoption and are not straightforward for everyone.
- Prioritization: Resources available for organization are hard to use. They struggle to understand which vulnerability they have to patch first.
CISA and SEI work aim to help organizations more effectively prioritize vulnerability management resources through use of Stakeholder Specific Vulnerability Categorization (SSVC), including prioritizing vulnerabilities on CISA’s Known Exploited Vulnerabilities (KEV) catalog. The solution relies on a risk-based vulnerability assessment approach that helps organization to choose what vulnerability are the most critical to mitigate in regards to their mission.
How to use SSVC ?
Stakeholder-Specific Vulnerability Categorization (SSVC) is a decision tree model. Its purpose is to prioritize remediation of vulnerabilities by looking at the impact on a particular organization.
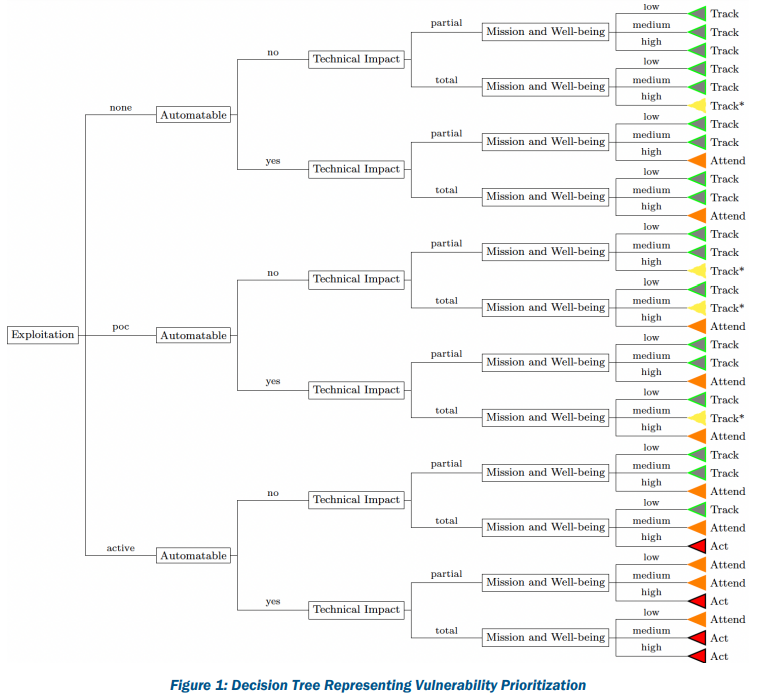
The three is composed of five decision points and four scoring decisions. CISA uses the following decision points and associated values for making vulnerability scoring decisions:
- (State of ) Exploitation: Is their any evidence of active exploitation of a Vulnerability ? The values are :
- None (no evidence),
- Public PoC (their is an exploit on ExploitDB for example),
- Active (Cyber Threat Actors use this vulnerability in the wild).
- Technical Impact: What is the technical consequences of the vulnerability ? It is similar to the CVSS concept of “severity”. The possible Value are:
- Partial (limited impact),
- Total (full control of the system).
- Automatable: What is the ease and speed for an adversary to use the vulnerability ? Vulnerabilities are not all automatable and are not always that easy to exploit. The possible values are:
- No (No reliable automation possible to identify, weaponize, deliver and exploit the vulnerability),
- Yes (Reliable automation possible to identify, weaponize, deliver and exploit the vulnerability).
- Mission Prevalence: How the essential missions of the organization are impacted ? Identifying Mission Essential Function (MEF) are a key part of business continuity and crisis planning. Their a three values for this decision point:
- Minimal (The component is not essential),
- Support (The component support an essential function),
- Essential (The component is an essential function).
- Public Well-Being Impact: How the exploitation of the vulnerability impact the human ecosystem ? The exploitation of a vulnerability and the technical effect it produce may impact physical, social, emotional and psychological of employee, customer or the wide public. The three values are:
- Minimal (The effect is below threshold defined by the value Material),
- Material (Effect on physical harm, environment damage, finance or psychology),
- Irreversible (Fatalities, Serious environment externalities, Financial crisis, Social crisis)
By using the CISA SSVC calculator or any similar system, the answer to each decision point leads to a spectrum of decision choice, called the scoring decision.
The vulnerability decisions and possible outcomes are:
- Track: No action require. This vulnerability will be remediated by simply applying vendor update.
- Track*: Monitor any change in the situation (exploit release, score reevaluation, …). This vulnerability will be remediated by simply applying vendor update.
- Attend: Operational management must be notice and further information can be requested to expert or the vendor. This vulnerability must be remediated as soon as possible.
- Act: Senior management must be notice and further assistance should be requested to expert or the vendor. This vulnerability must not wait for a vendor solution but require internal action to prevent its exploitation.
Scoring decisions greatly depend of the scope. An organization may apply different countermeasure depending of the prevalence of the mission of the observed perimeter. Including its public well-being impact. It is also very important to have so sort of software vendor management to establish a communication channel when necessary.
Conclusion
The Stakeholder-specific Vulnerability Categorization (SSVC) is a means of organizing and prioritizing responses for vulnerability management.
Vulnerability prioritization is important in cybersecurity because it helps organizations prioritize their efforts and resources towards addressing the most pressing security risks first. Vulnerability prioritization is often not feasible. Due to limited resources it is impossible for organization to address all of its vulnerabilities at the same time. While prioritizing vulnerabilities, organizations can focus on addressing the most critical vulnerabilities first, which can help reduce the overall risk to the organization.
There are several factors that can influence the prioritization of vulnerabilities. The potential impact of the vulnerability, the likelihood of exploitation, and the ease of exploitation. By considering these factors, organizations can prioritize their efforts towards addressing the vulnerabilities that pose the greatest risk to their systems and data.
Vulnerability prioritization is an important aspect of a comprehensive cybersecurity strategy. It helps organizations focus on the most pressing security risks and take proactive measures to mitigate them.


