Any business that has an online presence should comprehend the fundamentals of vulnerability and exploitability. There is no such thing as absolute security; there will always be a new, unanticipated danger, persistent vulnerability, or unexpected flaw. Both human factor and technical stack can make an organization vulnerable to attacks. It is impossible to eradicate every single attack opportunity.
However, it is not necessary to be faster than the assailant. The important thing is to be smarter than them. The main goal is to reduce the attack surface as much as possible, by first limiting vulnerabilities and then defending against exploits as mentioned above. This two-edge strategy will make sure that attackers find your organization a less attractive target, and that is the ultimate goal.
Vulnerability versus Exploitability : Sinews of War
Being aware of the distinction between vulnerability and exploitability can be beneficial when it comes to defending your system. This knowledge can enable you to focus on those vulnerabilities that can do real harm to your business (i.e., exploitability). It helps to keep your systems more secure by prioritizing vulnerabilities mitigation.
After identification and testing, any potential security vulnerabilities are added to the MITRE CVE glossary, a public catalogue. NIST, the National Institute of Standards and Technology, then examines the vulnerabilities, and all related data is included in the NIST National Vulnerability Database (NVD). In order for a flaw to be categorized as a CVE vulnerability, it must meet a prescribed set of requirements:
- Independent: The vulnerability can be fixed on its own without prerequisites of fixing other issues.
- Acknowledged: The software supplier know the vulnerability and recognize its risk.
- Proven risk: Evidence are attached to the vulnerability to prove its impact on security.
The CVSS is one of several ways to measure the impact of vulnerabilities, which is commonly known as the CVE score. This score between one and ten is designed to give an idea of how dangerous is the vulnerability.
The National Institute for Standards and Technology reported that in 2021, there was an all-time high of 20,158 vulnerabilities found. This was the fifth consecutive year that the number of vulnerabilities had increased and it is likely that this trend will continue into 2022. It is impossible to fix 20,000 vulnerabilities in one year, and it would be unwise to try and do so.
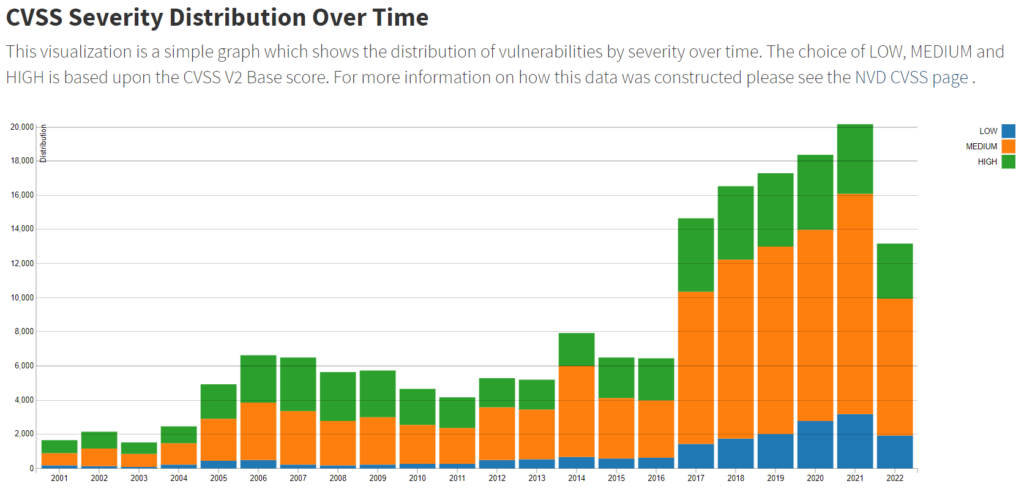
Visualization of the number of CVE released each year, broken down by its CVSS severity (source: NIST)
It might not make sense at first, but there are logical explanations for why it isn’t. One explanation is that current studies show that only 2.7% of CVE can actually be used by attackers. Various factors can explain why certain vulnerabilities discovered through security scanners and pentesters may not be that easy to exploit and therefore, do not present a notable risk:
- No exploit: If attackers wants to take advantage of the vulnerability, they will have to code themselves an exploit code. This reduce hugely the likelihood of the vulnerability to be exploitable by cybercriminals.
- Network Access: The vulnerability can be leverage, but in a specific context it may not always be at the adversary fingertips. It may be behind layers of firewalls or in an airgap network.
- Complexity: The vulnerability is not easily exploitable and requires a lot of conditions to run smoothly.
- Stability: The exploitable is very random and may cause crash without doing harm to the system.
Patching all vulnerabilities is not a wise use of time for those who already have plenty of duties. Additionally, even if you did patch every vulnerability in your system, it wouldn’t necessarily mean that hackers would be kept away.
Exploitability versus Exploited: No Mercy Triage
Numerous strategies exist for cyber criminals to breach an organization’s security, and many don’t necessitate a critical CVE or any kind of vulnerability to be successful. Phishing, spear-phishing, social engineering, exposure of credentials, default passwords are just a few of the tactics employed. A good illustration of this is the recent Uber hack which shows that hackers don’t need to resort to the newest CVEs or state-of-the-art techniques in order to compromise a business.
The first thing an attacker wants is that its operation succeed. If social engineering is more likely to work that a cutting-edge technical vulnerability, why bother? In addition, several factors may reduce the appeal of an exploitable vulnerability for an offensive operation:
- Does the vulnerability have an exploit proof-of-concept ?
If yes, then their is more chance to be exploited, because it is less vulnerability research. - Does the Proof-of-Concept has been included in offensive framework (Canvas, Metasploit, Elliot or Dsquare) ?
If yes, then their is more chance to be exploited, because you have a more stable weapon. - Does the vulnerability enables Arbitrary Code Execution ?
If yes, then their is more chance to be exploited, because you can inject your own malicious payload. - Does the vulnerability is exploitable via remote access ?
If yes, then their is more chance to be exploited, because you can take advantage of it without gaining a first access in the network. - Does the vulnerability applies to web technology ?
If yes, then their is more chance to be exploited, because most of companies have an internet presence. - Does the exploit code can cause a memory corruption ?
If yes, then their is less chance to be exploited, because the attacker increase the risk of crash and detection.
Patching is vital for upholding a robust security stance and is an integral part of every security plan. The problem, however, is that many tools currently prioritize solutions based only on the Common Vulnerability Scoring System (CVSS) scores, and what is overlooked is the organizational context; obtaining knowledge on how to differentiate the significant 3% of vulnerabilities from the remainder of the 97%.


